Mirai IoT Botnet Strikes
by AKM
Posted on January 30, 2017 at 11:34 AM

Mirai Takes Over Millions of IoT Devices
Let's start off with some background knowledge; IoT stands for "Internet of things". Essentially they are devices like microcontrollers that are always connected to the internet. Most of these devices are reset once turned off and back on again, which means that all tasks are stored in a RAM like setting. To disinfect, all you need to do is restart the system, but do keep in mind once it connects back to the internet, it is re-infected within seconds. This also means that most of these devices have hard-coded passwords. Some of these "smart devices" can be lightbulbs, vending machines, etc. Some of these devices are also opened to the entire internet. Hard-coded passwords, open to the internet, sounds like imminent cyber disaster? Indeed.
So now that we understand how IoT devices work, let’s get straight into how Mirai intervenes. Every device Mirai hijacks is using some form of Linux. Most of the devices that are infected by Mirai are IP Cameras and routers. This isn’t the first time IP Cams and routers have been under attack, there have been many exploits dedicated to bypassing web panels, etc. attached to these devices for easy accessibility. What makes Mirai special is how it is deployed. Mirai has its own set of hardcoded passwords that specific manufacturers place inside their devices. After Mirai infects these devices, they all begin scanning IP addresses looking for more IoTs to infect. This gives Mirai a “self-replication” capability that makes it fast spreading. With all the IPs being scanned at once, there are certain IP addresses that are blacklisted within the Mirai source code, and they all seem to be government related. Most likely done to evade law enforcement detection in some form. Once a decent amount of IoT devices are infected, they can all be ordered to start sending traffic to a site, essentially launching large scale DDoS attacks.
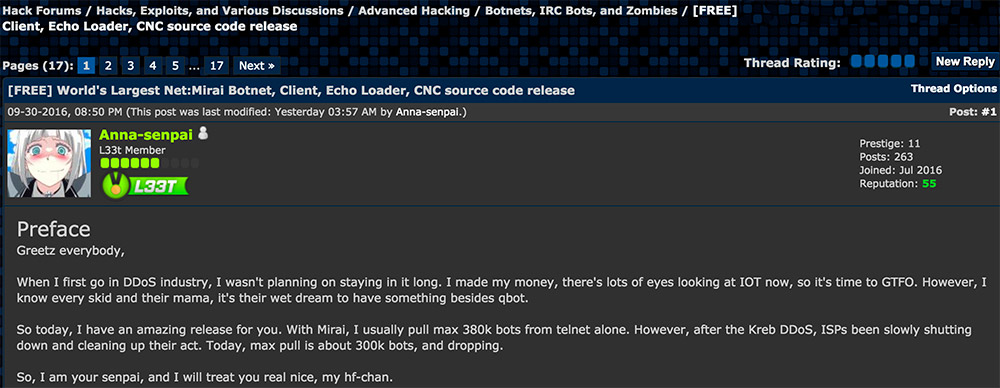
Mirai’s source code was initially released on a forum called HackForums. A user with the name “Anna-senpai” seems to be its author. Anna seems to reference Qbot in his post, a popular C program amongst those with low-end programming knowledge. Qbot (otherwise known as lizkebab) was a widespread, overused, piece of “malware” that exploited a flaw in bash shell that dates back in 2014. The fact that it’s being used still to this day tells users like Anna that 1. There is a huge market out there for DDoSing and increasing bot count and 2. There are still many devices out there that are affected by such flaws and vectors.
Edit: Anna’s own identity seems to have been revealed by a post made by Brian Krebs.
Alas, tools like Mirai remind us that our infrastructure is being filled with unnecessary appliances that cause more trouble than help. Think about it, does your coffee maker really need internet capabilities? Doesn’t it worry you that such items are easy to control and access remotely? In before we see ransomware being developed to keep items in our fridge hostage, we should think twice about what we leave open to the world.
InfoSec Related