Inside North Korea's Internal Network
by AKM
Posted on November 10, 2017 at 5:45 PM

North Korean Intranet
With the light of all the political threats that go back and forth daily, we are more intrigued on North Korea’s presence. A country that’s completely isolated from the rest of the world, one might ponder what their internet looks like, if they even have access to that type of tech. Surely they do, I mean how could a country have access to nukes but not the internet? Well here’s your answer.
A little background information, North Korea's internet is all internal, which makes sense. If you want to completely isolate your own civilians from the outside world, you must apply this digitally too. The proper term for this type of network is "intranet", basically internal-internet. This intranet has a name, Kwangmyong. Regardless of its isolation techniques, it’s nothing quite like the normal internet. Some of its internal sites contain e-libraries, emailing service, even a social media platform (which we will get to later). The only way to access this network is from within North Korea. So how does this all play out?
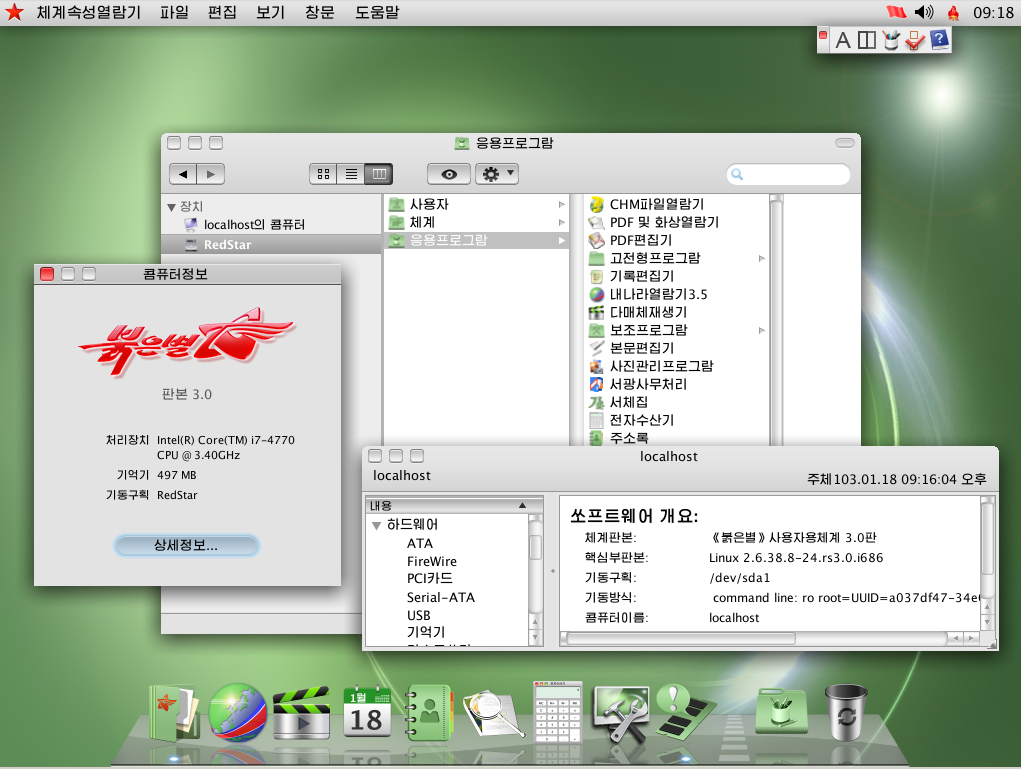
North Korean Browser and OS
Yes, you read that right. Alongside an internal internet, is a complimentary browser used to access it. Now this browser is based off of Firefox, (a very old version of Firefox) it's called Naenara. This browser comes with Red Star OS, the official North Korean operating system (based off Linux and uses KDE as the desktop environment). It's made to look like Apple's OSX. The decisions for its aesthetics are rumored to come from Kim Jong Un's own taste in Apple products.
Red Star OS never always looked like the screenshots taken above. It actually used to resemble Windows XP in earlier versions. So why would the North Korean government want its civilians to use this software specifically? I think you may have answered the question.
Red Star OS has a small little twist, it has no root. That's right, root has been removed. Many Linux users are familiar with what root is, essentially, it's a user account equipped with the highest level of authority on a machine. It allows a user to launch commands that are deemed sensitive, like installing applications, etc. So why would the North Korean government not want you to have root?
Well, ideally if you had root it’s quite possible you’d be able to break some of the operating system’s own restrictions. You might be able to reverse engineer some of its programs to access further parts of the intranet network that you’d normally be restricted from. Perhaps access to the internal IP of some nuclear silo? (assuming this is all client based).
Upon launching Naenara (the browser), it makes a request to a site located http://10.76.1.11/. No, you cannot access that site remotely, it’s an internal IP address. Now with a few networking tricks, we may be able to get a feeling of how the intranet looks like.
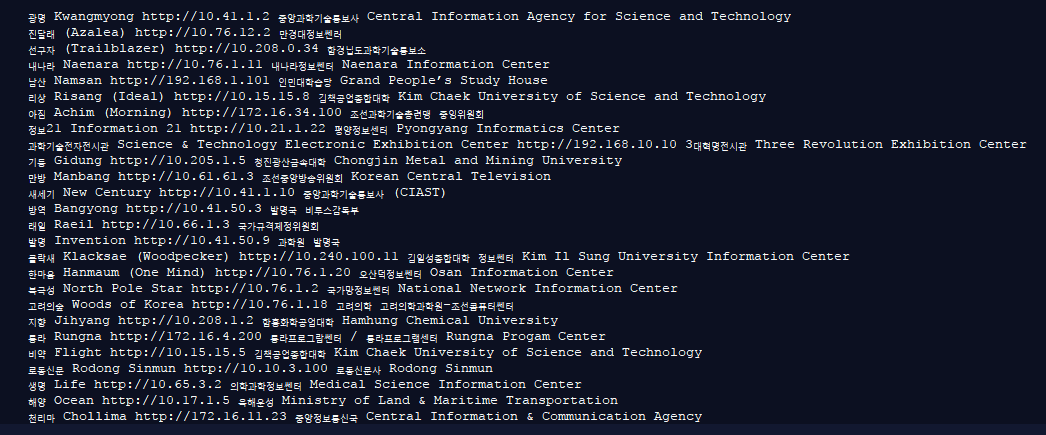
Here lies an internal IP network map of North Korea’s intranet. This is actually a huge chunk of metadata that resolves what’s behind each internal IP. This data was obtained directly from North Korea thanks to Aram Pan, one of the only few foreigners to travel inside one of North Korea’s computer facilities.
North Korea's Intranet is all internal. The sites are all controlled by internal IP addresses and are only accessible through people within. What's interesting is not the internal IP addresses, but the external ones within North Korea. About 1,024 IP addresses are assigned to North Korea. These external IP addresses can be used to both host information and also access information from and to the real, global internet. Only a few people (higher classmen) have access to the real internet. It’s relatively limited, very small IP reservation block. This makes North Korea prone to nation-wide DDoS attacks.
It doesn't take much resources to shutdown Internet access in the entirety of North Korea, in fact, the United States Cyber Command volunteers daily on making sure North Korea does not receive internet access via DDoS attacks. Not to mention, North Korea’s internet is all routed through satellites belonging to China. This isn't the smartest move in terms of intelligence gathering. Some of these external IP addresses are real servers located within North Korea. In fact, some of these external IP addresses link to actual webservers. Sites from North Korea that you can visit right now.
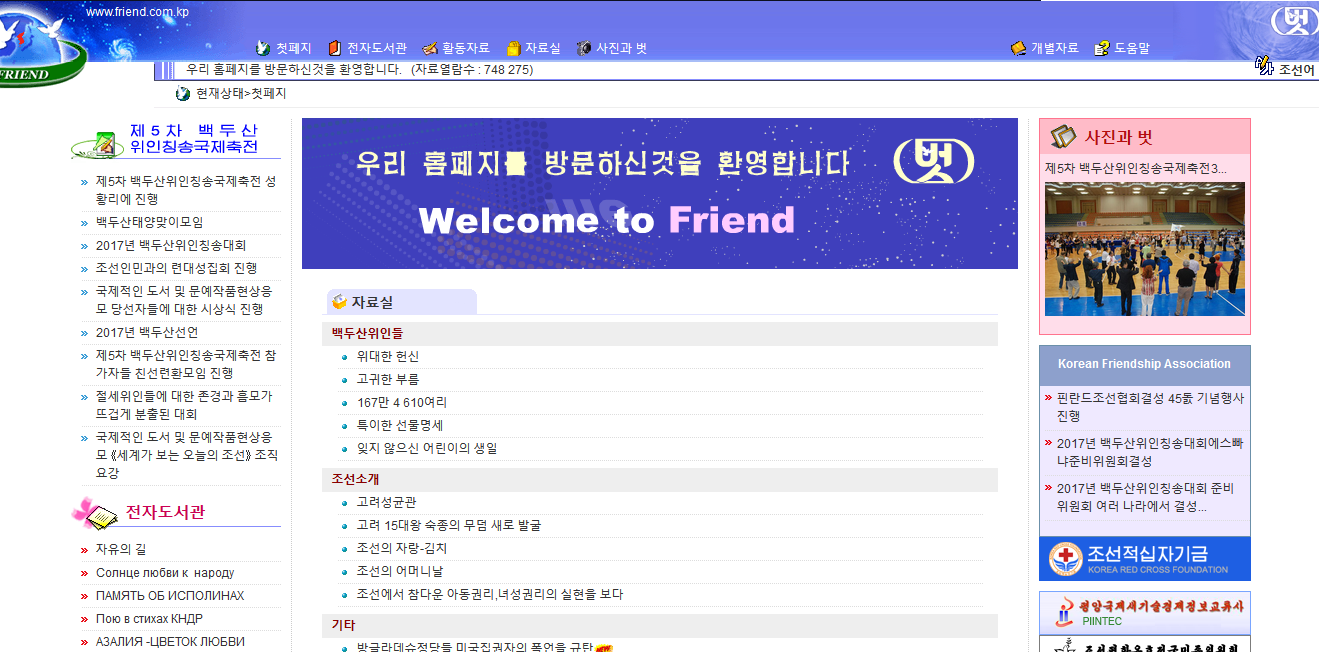
Remember that social media platform I mentioned earlier? Behold. This site is located inside North Korea and you can visit it yourself right here. If you were to ping this site, you would resolve the DNS to an IP that falls under North Korea’s external IP block.
Only a handful of sites belonging to North Korea exist, most of which use com.kp domains. Yes, if you haven’t figured this out already, all North Korean sites are formatted in the Korean language. So why would any of this stuff be accessible externally? Wouldn’t that risk the sole purpose of total isolation? Yes. It would. Actually it might have already.
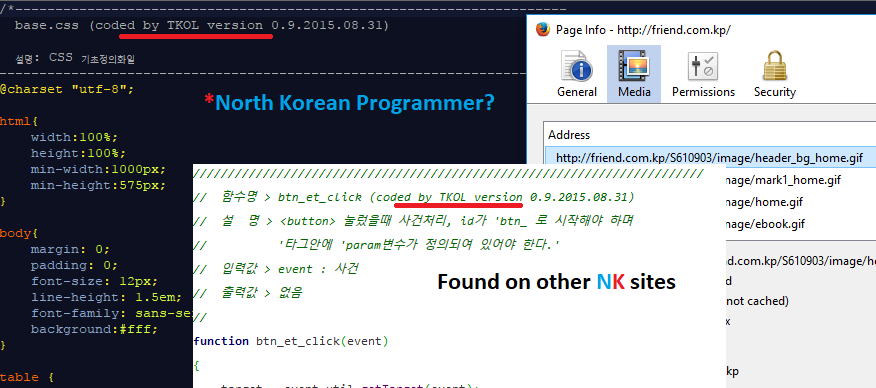
Upon further investigation of that same exact site, I read through some of the source code behind some pretty basic CSS and JavaScript. Embedded within the sites source code are some interesting comments. More than one North Korean site had the metatag “coded by TKOL”. I’m personally not sure if TKOL is some vendor or an actual programmer. It gets more interesting.
I tried looking for more references to “TKOL” and couldn’t find anything. I came across a Pastebin post but it seemed like whoever that had posted it was doing the same thing I was, scraping metadata from these North Korean webservers. So who is TKOL? Could he really be a programmer who resides in North Korea? One would assume this to be some sort of alias.
Now how clever would it be if he were to write more comments like this only asking for assistance or maybe even help from the North Korean regime. It’s one of those things that will unfortunately be left unanswered for years to come.
InfoSec Related