Nicehash's Dirty Little Secret
by AKM
Posted on December 8, 2017 at 12:15 PM

Nicehash's Origins and Background
Nicehash, one of the leading mining platforms has been hacked. Approximately 4,736 bitcoin valued currently at 70,631,418 US dollars has been stolen. These funds were all part of Nicehash’s own wallet system. Nicehash’s mining platform allows users to create their own wallet on their platform in order to receive payouts at a sooner time, usually within a week. It was a perk in order to get users to use their wallet platform.
In order to actually use Nicehash, the only data that is required to be given is a bitcoin address. No user logins were necessary for miners (unless of course you choose to have a bitcoin address on their platform for faster payouts). From what it seems, all the bitcoin stolen came from that specific sector of their internal systems. Here’s what happened according to Nicehash’s own CEO and CTO.

Nicehash's Security Breach and Statement
Marko Kobal alongside Matjaz Skorjano made a live video on Facebook to address some of the burning questions users may have on their stolen funds. 70 million dollars is clearly no joke, this type of heist would have to be sophisticated no? Actually, not very sophisticated at all. According to Kobal, Nicehash has over 250,000 active users on their platform, Nicehash has paid over a billion dollars in funds from the time of Nicehash’s creation (according to their about page, over 128,000 coins have been paid out). So clearly there is a huge targeting vector here. To any hacker or group of hackers, Nicehash is the perfect candidate to compromise.
According to Kobal, at approximately 1:00 AM December 6, 2017; A hacker or group of hackers infiltrated Nicehash’s internal systems through the company’s own compromised computer. According to their VPS logs, at approximately 1:18 AM central European time, there was a failed login from an IP outside the EU. A successful login was then initiated through an engineer’s own login. At this time, the hacker(s) managed to “learn and simulate the payment system” on Nicehash’s internal systems. At approximately 3:24 AM, the first round of transactions started to roll out.
There are multiple flaws with the story that’s coming from the CEO here. The bitcoin address that received all the funds is located here. Within the statement made on the video, there is a possibility of multiple addresses used, but from what we’ve seen on the bitcoin address: 1EnJHhq8Jq8vDuZA5ahVh6H4t6jh1mB4rq; it appears to contain all the coins that were initially stolen. All sent to one bitcoin address in multiple transactions. In this post made by Nicehash’s own Facebook page, the service was in maintenance; an hour later they made a post about a security incident located here. So the response time after the breach was around an hour which isn’t that bad. Here’s what’s alarming about the story.
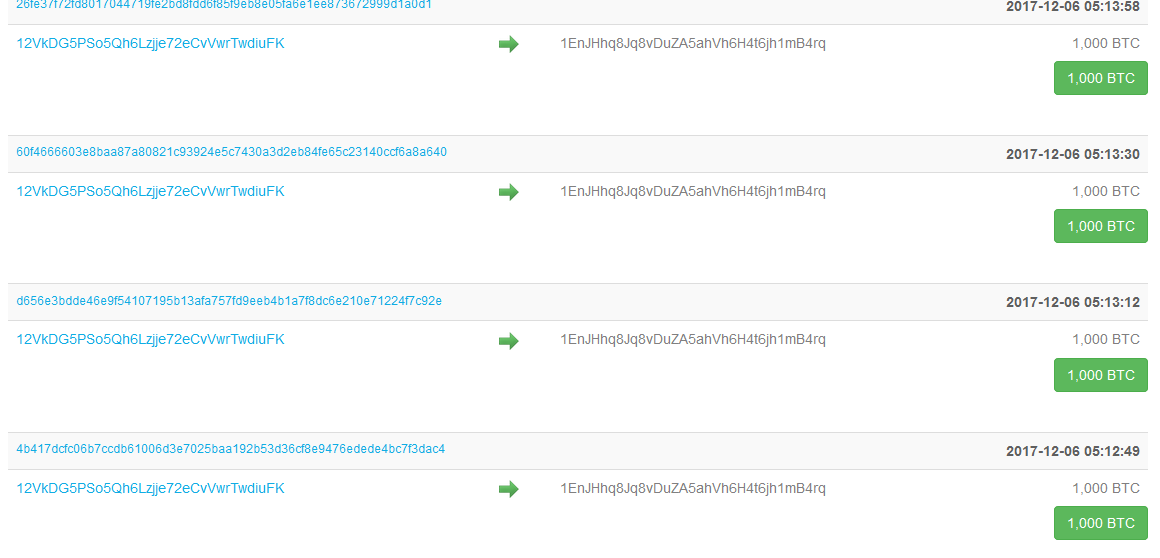
The entire heist took around 3 hours to complete. From the time the computer was compromised, until the very last coins that were sent out. Not only that, but this hacker that compromised an engineer’s computer (very easy through phishing and other remote access methods), would had to have learned how Nicehash’s systems work. The hacker(s) involved would have to have known quite well the internal systems in order to pull this all off. If we take a closer look at the way in which all the bitcoins were extracted, the first coins were sent out on 2017-12-06 05:05:10 and the last coins were sent out on 2017-12-06 08:42:03. Essentially, regardless of the time zone, it took nearly four hours. This entire time, the system admins didn’t notice anything? How could that possibly be. A platform that deals in such high volume of transactions doesn’t have any bells that ring whenever transactions weighing around 1,000 bitcoins is sent in time intervals? Just look at the blockchain transaction history of that bitcoin address and tell me that the payment time intervals don’t look suspicious.
Kobal claims that Nicehash has notified local and international law enforcement agencies and also a multitude of security experts. He also claimed they have notified all major exchanges and mining pools in order to get the funds back. Let’s be realistic here, the funds are not coming back. Period. This is in the nature of bitcoin, transactions are not by any means reversible. The only way to get those coins back is to have the private key associated with the public key shown earlier. This whole story is shady, but it gets even worse.
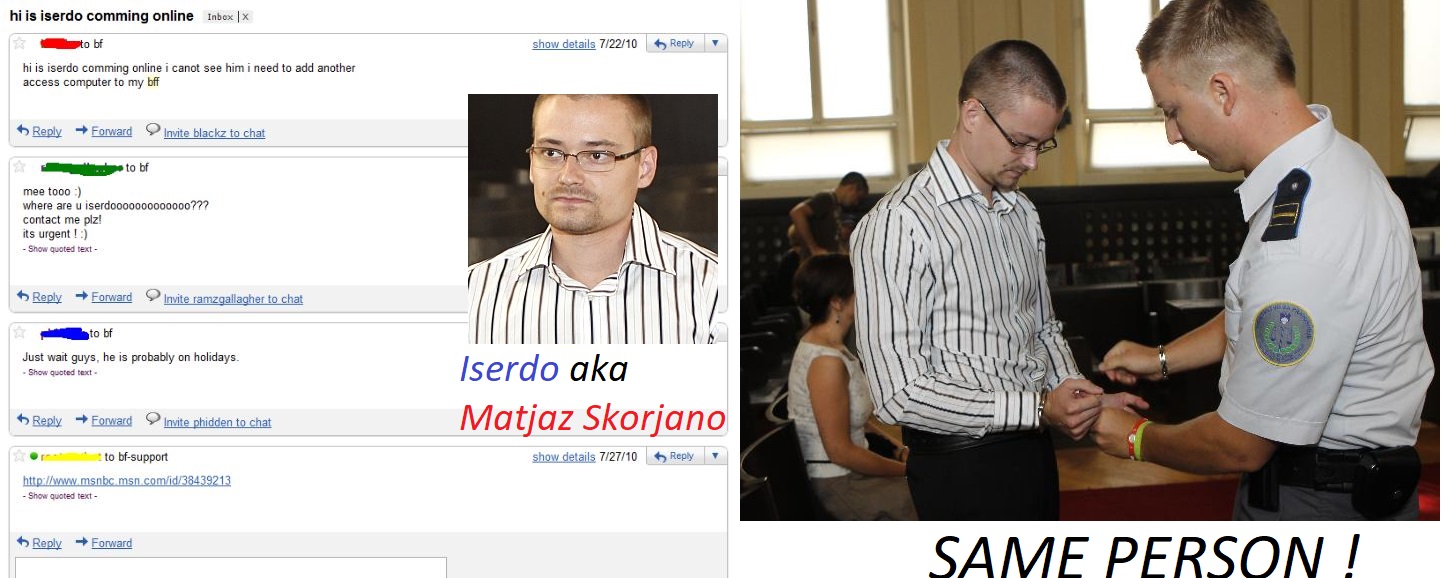
I’m sure many of the readers here are well aware of what Darkode is. Darkode was an underground community forums for hackers all around the world to sell exploits, malware, etc. The marketplace was very successful until FBI’s conjoined Operation Shrouded Horizon which arrested some key individuals of the Darkode project and took the site offline. So how does all this tie in? In the video made by Nicehash, we see two individuals, CEO and Co-founder Marko Kobal, and CTO Matjaz Skorjanc. Let’s take a closer look at Matjaz; according to Kobal, Matjaz is the original author and core developer of Nicehash. Pretty big title in Nicehash. Let’s just google. We come across a blog post made by Brian Krebs located here. Matjaz Skorjanc aka Darkode core member Iserdo, has a very valued malicious past from what it seems. Involvement in Darkode and as the primary author behind the Mariposa botnet (more information about the botnet can be found here). Matjaz was arrested and found guilty in 2010, here's an article that details all of it. What is this guy doing as the CTO of Nicehash? Very suspicious how he was arrested in 2010, but Nicehash was created in 2014 (that of which he was a core developer to).
So now we know that the CTO behind Nicehash has involvements in Darkode. Okay? Maybe he’s a changed man? Let me explain how bad this is. Darkode started in 2007, and ended in 2015. Nicehash started sometime in 2014. Usually CTO’s are present during the creation of such platforms. So for his position, we can only assume he was around during the same time that Darkode was also live. Now this is all healthy criticism of the platform that anyone looking at this would assume. There is a possibility that this was all an inside job no doubt.
How could 70 million dollars be stolen and for them to remain so calm about it. This could very well be an exit scam. The method in which this all took place, for someone to learn the insides of Nicehash only in the matter of hours, none of this adds up. You can find more malicious information about Matjaz Skorjanc by simply searching, his history stretches far beyond Darkode. Nicehash will begin continuing its service soon, and all the stolen funds will be forgotten and never returned just like all the other platforms that get hacked over time.
InfoSec Related