Our Philosophy and Motive for releasing PoC code
by AKM
Posted on January 3, 2019 at 5:39 PM
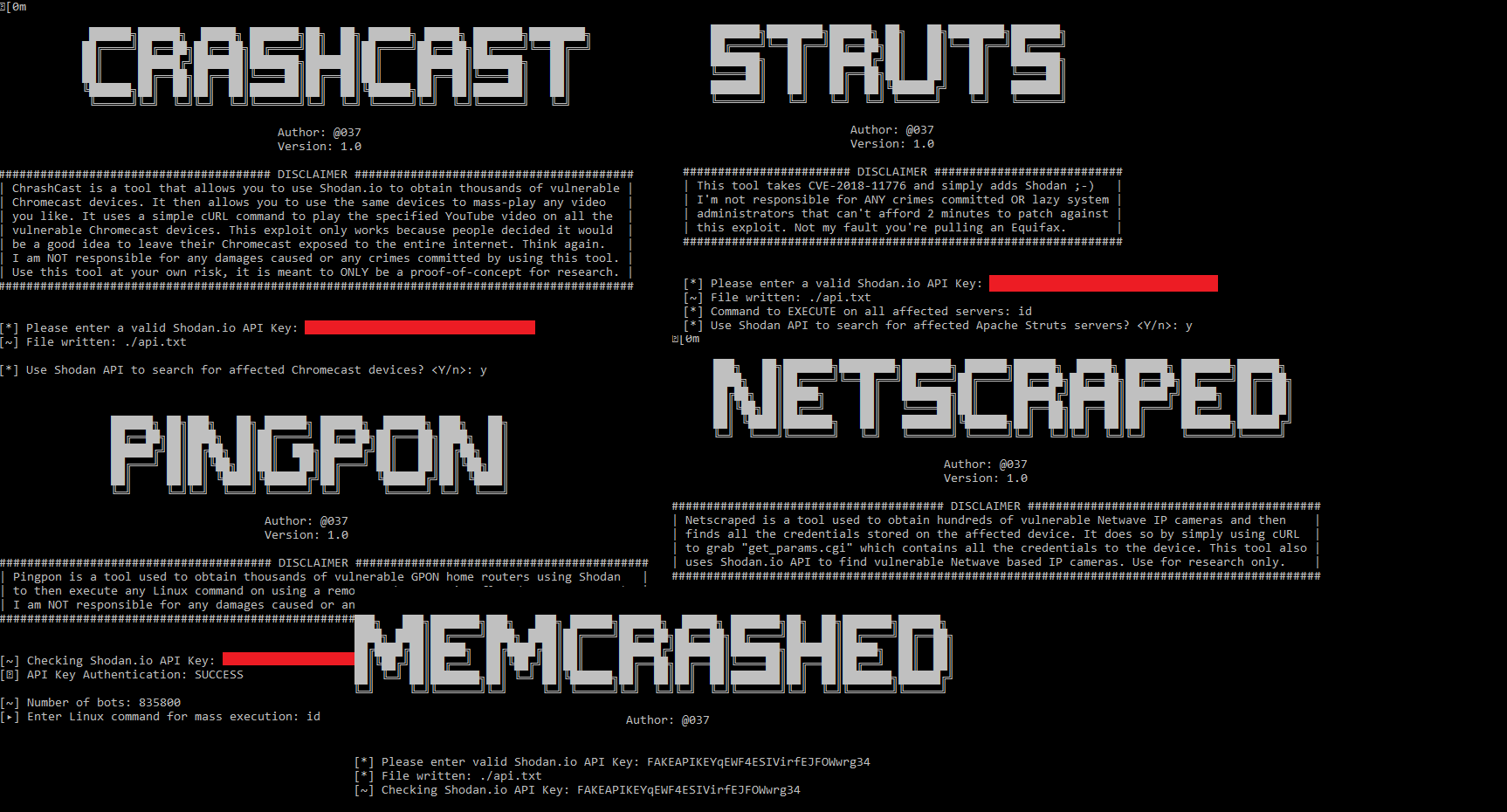
I wanted to create this post to solely address some things that have been floating around. Specifically behind our motives for releasing exploit code to the public. You see that image above? That's a picture of all the exploit code we've released over the year. What's one persistent element in all of the exploits? Shodan. Now why would we want to do that? Surely people get the idea? No. That's the issue we're going to resolve in this post.
For almost a year now, we've been doing the same thing over and over in high hopes that people will learn the valuable lesson of not putting shit on the internet. Things that don't need to be exposed, like a hospital's SMB server. Because when things like this are happening, and that hospital gets infected with something like WannaCry, everyone starts to lose their minds! We never take 5 seconds to ask, why the hell does a hospital have SMB exposed to begin with!
Remember Memcached? The flaw that allowed record breaking DDoS attacks to be initiated? We're talking Terabytes per second here. Who was to blame? The people who used exploit code to initiate the attacks or the lazy system admins that wouldn't take their servers off the internet? I'll let you answer that one. It's a question of ethics. Nevertheless, if the exploits where never made public, the lazy system admins wouldn't worry, they wouldn't care. I mean let's go back in time even further, what about Equifax? Remember that? Who really cared here, the victims? Or the security teams? If you say security teams, then why was there over 30 webshells on their webserver? Why didn't they patch for MONTHS? Do they care? No. Not until something happens.
That's what we're trying to prove to you. By all means, all we're doing is releasing PoC code, that's not illegal. Using it against systems we own, that's not illegal either. But using it against systems we do NOT own, now that's 100% illegal. That's where we draw the line that will never be crossed. We don't even test the exploits we release (only on local machines). We release it for a researcher audience group, we release it to raise awareness. The type of awareness that causes the public to react, to patch, to take things off the internet.
When services like Github get attacked by a lazy system admin that isn't taking his/her Memcached server offline (or at least not exposed to the entire internet), who do we blame? If you ask me, I think the sysadmin should be fined at the bare minimum. The lesson here is that people will never learn until something happens. In this world of internet of things, this is the only way to keep insecurities at bay. Some may say it's unethical, some say otherwise. But if we don't continuously check for misconfigurations, out-dated systems, then when things like WannaCry happen, we blame everyone but ourselves for allowing it to happen. Hacks are meaningless had it not been for the admin or creator who allowed them to happen. It's like leaving your car window open and complaining when you get robbed. Be smart. Be vigilant.
Unfortunately, a couple Chromecasts or printers isn't going to raise much awareness. That's why we've built better tools. Tools that I think many of you will appreciate the sweat and tears for coding it. Many of you are here for all the exploits we release, I'm hoping you find our better applications instead. Here's one;
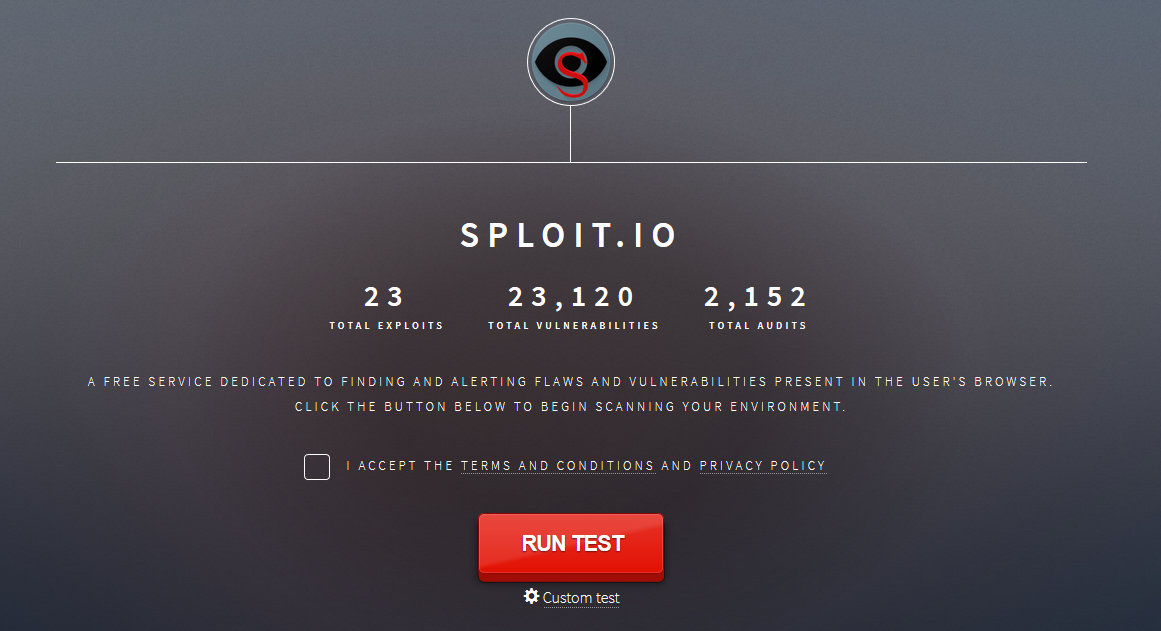
This is Sploit.io. I haven't gotten the chance to actually address what it is, and what it does (I will do that in a later blog post). This system essentially tells you exactly what's wrong with your browser, but it does it much better than any site out there! It tells you the actual CVE of issues tailored to your browser. It also gives you real exploits that work against your browser (doesn't execute, but gives you a button to test it out on). It warns against VPN leaks, Flash vulnerabilities, Spectre/Meltdown checks, and much more!
In the weeks to come, I have a lot of things to release (non-exploit orrientated, because I know that's what most of you are here for), just be patient, I promise you won't be disappointed.
InfoSec Related