Sploit Check: Avast Browser
by AKM
Posted on June 7, 2019 at 4:50 PM
Source: Avast
Avast Secure Browser Analysis
Avast, the self-proclaimed "global leader in digital security products," has released a new version of its Avast Secure Browser. It promises people "even greater protection and control over their privacy, identity and personal data when browsing the internet." (Avast News Release). One statement is standing out in the announcement: "The new version introduces [...] enhanced Anti-Fingerprinting to prevent websites from tracking people as they browse".
That got my attention. There are so many ways browsers can be tracked today, how does this company make it all stop, I wondered - and decided to find out. Using sploit.io as a benchmark, I focused on three core features highlighted by Avast: its browser’s anti-tracking/fingerprinting capability and its malware and phishing detection features.
Avast Secure Browser is promising me three things:
- "Stay anonymous: Our built-in privacy features hide your identity and cover your digital footprint, so no one can track you."
- "Browse faster: We automatically block annoying ads while you browse, because less to load means faster."
- "Secure your personal info: All the security features you need to stop malware, phishing scams, and identity theft."
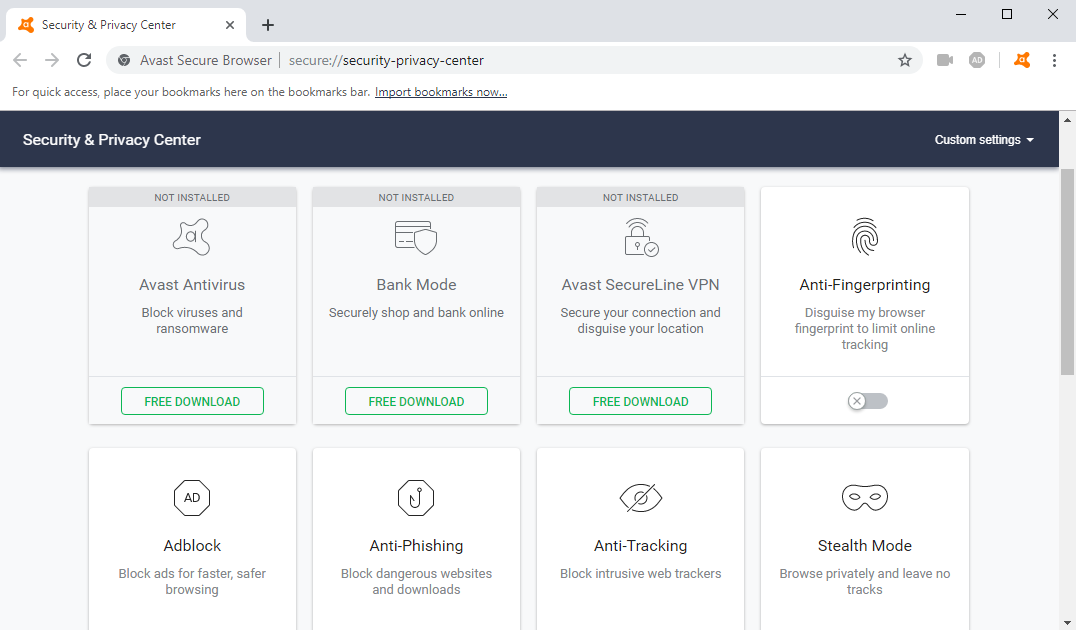
Avast Security & Privacy Center
Avast comes with a "Security & Privacy Center" for enabling/disabling their set of features. They have an anti-fingerprinting feature (disabled by default) and it promises to "Disguise my browser fingerprint to limit online tracking". Bear with me, we’ll put that to the test shortly. They also have an "Avast SecureLine VPN" which masks my connection, a "Bank Mode", and their "Antivirus", all of which do not come preconfigured and require a download.
I ran the browser against sploit.io and the results were sobering, even if I didn't have the highest expectations. First of all, Avast Secure Browser is based on Chromium (version 73.0.3683.86). The security model is solely dependent on Chrome, which isn’t bad, but it also means Avast isn’t really doing anything to Chrome to make it "more secure" besides what’s offered in the Security & Privacy Center. If Chrome had a working exploit, Avast Secure Browser would also be vulnerable to it.
I then went ahead and enabled their "Anti-fingerprinting" feature (which was disabled by default since it can cause problems with normal website loading) but disabled everything else because I wanted to see if it can by itself block/divert fingerprinting without the other features affecting the results.
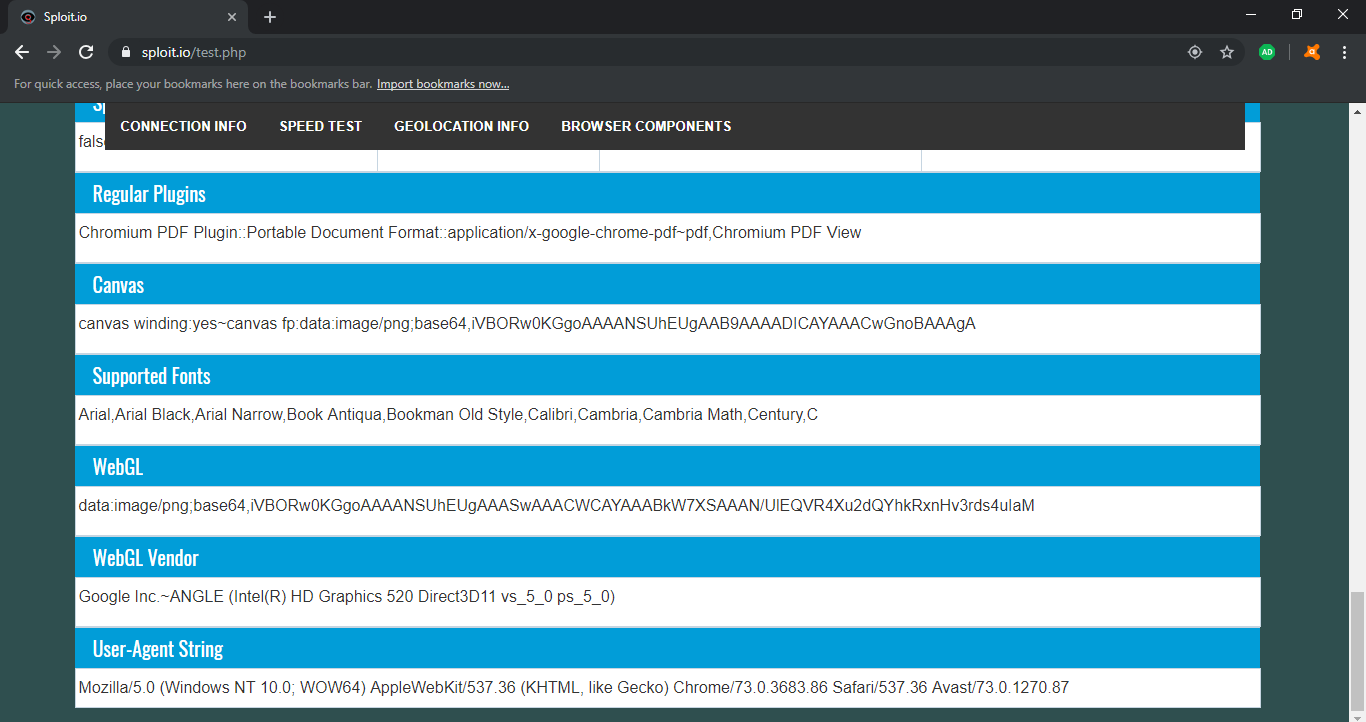
I ran a test with Anti-fingerprinting enabled, then another test with it disabled. I noticed only a couple differences that show me exactly how they’re "evading" fingerprinting. When I enabled the anti-fingerprinting feature, it set my WebGL and WebGL vendors data both undefined. These two variables reside in JavaScript and can be accessed by any site and help fingerprint the browser. Unfortunately, WebGL is one of many methods used to fingerprint the browser using Javascript.
There are other variables besides WebGL that can help fingerprint, and Avast doesn’t block or spoof them. In fact, with just Javascript, I was able to fingerprint myself through Canvas, supported fonts, and audio buffers alone.
When the anti-fingerprinting feature is enabled, Avast Secure Browser changes my browser plugin data, the data that determines what plugins are readily available for sites to take advantage of. It changes it from the string "Chromium PDF Plugin::Portable Document Format::application/x-google-chrome-pdf~pdf,Chromium PDF View" to their own "Native Client::::application/x-nacl~,application/x-pnacl~". This doesn’t accomplish anything besides tell the website that there is no Chrome PDF plugin enabled. The site can still determine I’m running Chrome through the user agent string.
Based on my findings, the anti-fingerprinting feature tries to make Avast Secure Browser appear like your garden variety browser. Because it doesn’t block/spoof everything when fingerprinted against, it’s fingerprinted using the other available non-blocked components. This feature does in fact change the fingerprint hash Sploit computes, but nevertheless, the newly generated hash can be used to track the same user, if they happen to have the anti-fingerprinting feature enabled persistently in future sessions.
Anti-fingerprinting? Does it work?
Besides those two minor changes, everything else that helps fingerprint a browser stays exactly the same. In my opinion, Avast's "Anti-fingerprinting" feature is completely useless because Sploit still manages to persistently fingerprint my browser with or without that feature enabled through other means.
I did however notice that Javascript is in fact processed properly ONLY if you have their "Anti-tracking" feature enabled, which blocks certain Javascript elements that prevent the browser being fingerprinted through Javascript only. It’s almost identical to the way NoScript (a freely available extension) behaves. If this feature is disabled, every javascript element, fingerprinting methods, cryptojacking scripts, clickjacking, et al. are all possible even with all their other security features enabled.
It’s important to note here that Javascript is NOT the only way to fingerprint a browser. There are other non-Javascript ways to fingerprint like using your user agent string, IP address (both IPv4 and IPv6), content encoding (part of HTTP header), language preference, timezone, screen resolution, architecture type, even with CSS. Sploit was able to grab all that information with ALL security and privacy features enabled, which still allows the Avast browser to be fingerprinted.
One thing that caught my eye was their "Stealth mode", and oh boy, this is hilarious.
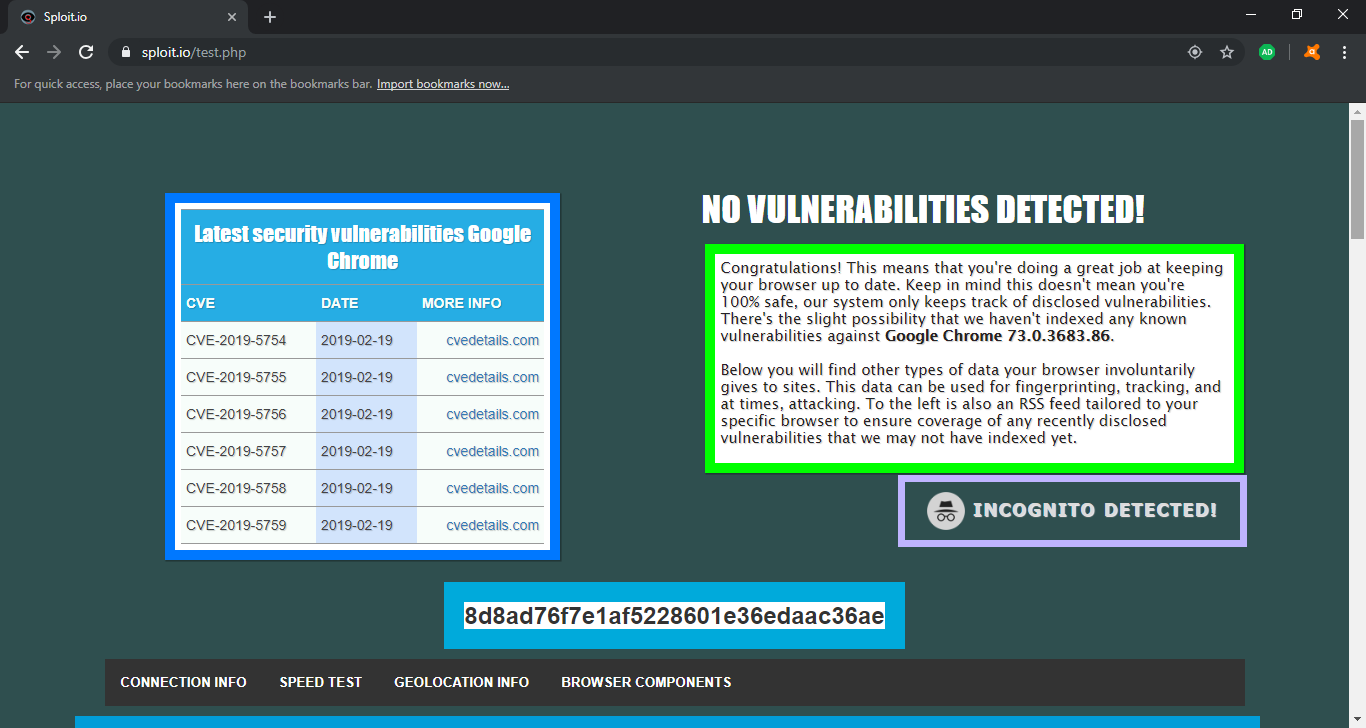
Avast's "Stealth Mode"
So what’s up with the Avast Secure Browser’s "Stealth Mode" a.k.a. Google Chrome Incognito mode?
I can’t pinpoint any differences between Google’s incognito mode and the Avast stealth mode. The worst part is, Sploit detects the Avast stealth mode as being Google’s Incognito mode. It does this by checking the availability of some Chromium API features not present in incognito mode. And if you look carefully, there is a fingerprint hash! So what exactly is so stealthy about this? I have absolutely no idea.
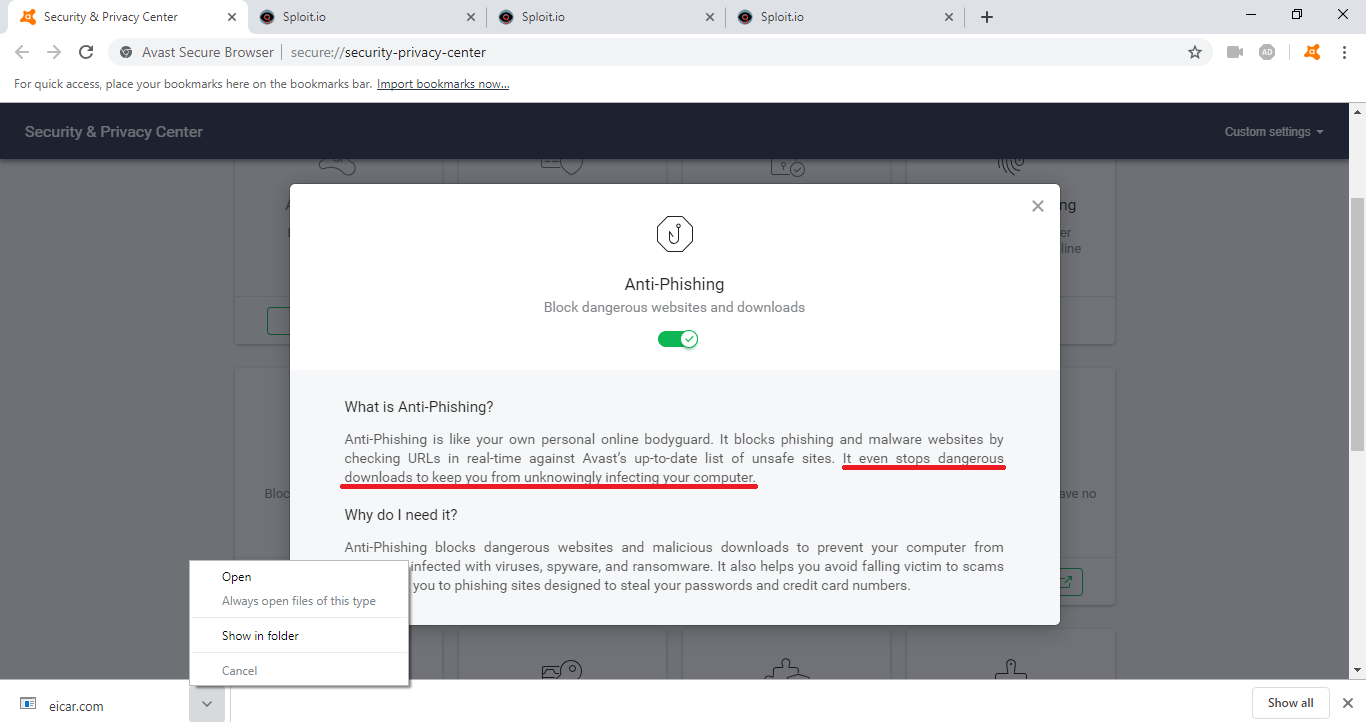
Avast Secure Browser vs. Malware
I thought to myself, okay, this is Avast. They have decent antivirus software, so surely they will detect any malicious binary I try to download onto my machine. Nope. I ran an eicar test; and for those that don’t know, Eicar is like an antivirus standard binary in which you try to hide it and if your antivirus can’t detect it, the antivirus is no good.
Think of it like a test virus, only it’s not malicious at all and every antivirus software recognizes it as being malicious. I downloaded the eicar test binary and nada. Nothing happened. It installed as normal, no Avast popups or anything. It took around 3 seconds before Windows Defender had to warn me against it, but Avast did nothing.
In the picture above, you can see I even have their "Anti-phishing" feature enabled and it claims that it "stops dangerous downloads". Perhaps they whitelist eicar (not sure why they’d want to), but who knows.
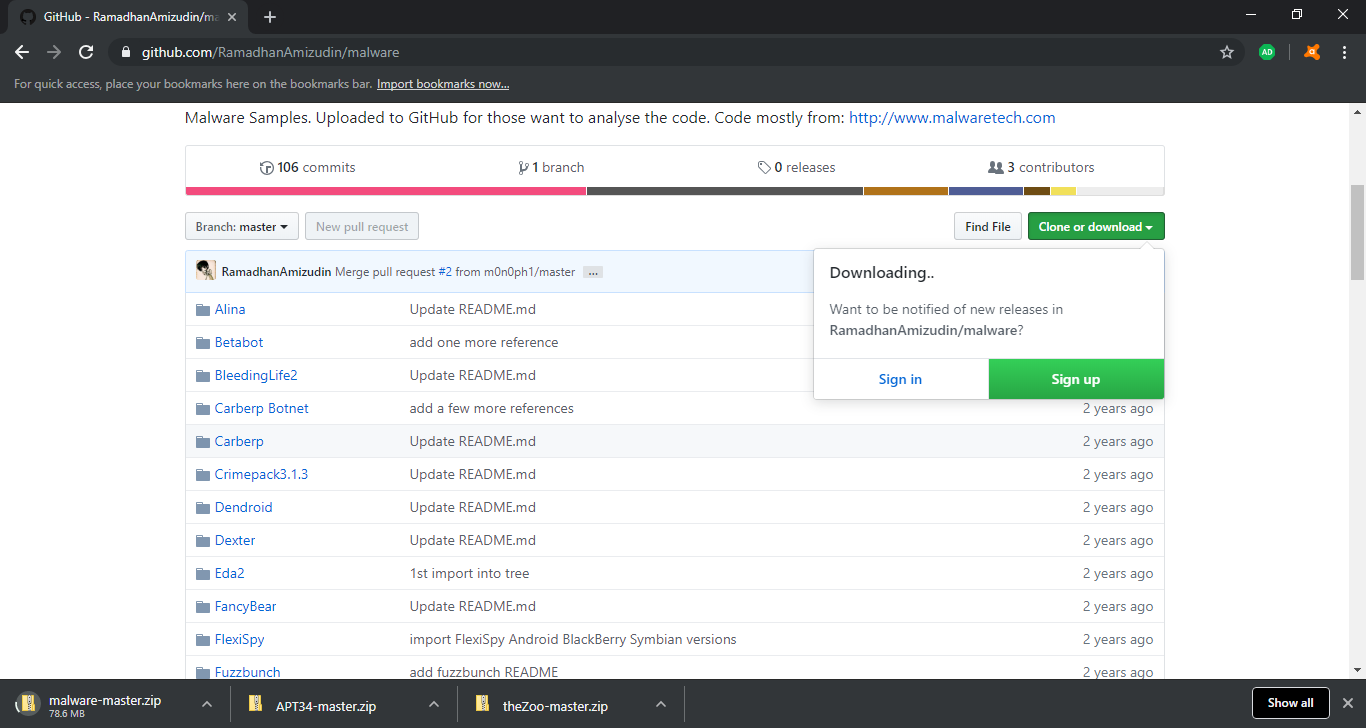
So I thought, okay, the only way to truly test if the browser can catch some malicious binaries is by downloading some real malicious binaries. I went to github and searched some of my favorite repository archives that are filled with malware for researchers to analyze.
I downloaded not one archive, but many. These archives have tons of malware inside them, from WannaCry to Stuxnet samples. Not a single zip file was detected. Maybe because it’s inside a zip? I put them in VirusTotal, and it had no problem identifying the archives as malicious. Avast Secure Browser wasn’t able to detect a single archive I downloaded.
So what’s the verdict? Well, on my personal test bench, Avast Secure Browser wasn’t able to stop fingerprinting and it wasn’t able to stop malicious downloads. Perhaps it’s able to stop phishing as advertised: "All the security features you need to stop malware, phishing scams, and identity theft". I went to a few phishing sites to find out and I was granted what looked like similar to Google Chrome’s phishing warning (but not identical). I’m not sure how their anti-phishing feature blocks malicious sites; a lot of anti-phishing works off of "URL filtering" (by processing what sites/URL you visit to determine if it has been flagged rather than looking at the site content for heuristic/signature style detection).
So should I use Avast Secure Browser? To me it looks like I’d be better off with just Chrome. The protections it offers just aren’t that good. If anything, it’s like Chrome with a few extensions installed which I can do myself without having to install this entire browser. Go get NoScript extension and you’re at the same level as Avast Secure Browser, as it offers nothing earth-shattering more in my opinion.
P.S.:
You’re probably wondering, well geez, why not use the Tor browser? Isn’t that a good alternative? The short answer is yes. The reasons why I don’t use Tor are:
- Most websites can see that you’re using Tor by simply looking up the exit node you’re connecting with.
- Cloudflare hates Tor, and I’m sick and tired of having to fill out a million captchas just to visit one page at a time.
- You’d be surprised at how many exit nodes are already setup for passive MITM attacks when you’re not using HTTPS, and how many of us really look to see if it’s always 100% there and we’re not susceptible to any SSL downgrade attacks? Not many. (Check out this diagram made by the EFF for a better visualization).
Last but not least, almost any forum you try to access with Tor will have your requests blocked, so I can’t really do any of my research work.
InfoSec Related