Blackhat USA 2018 Recap
by AKM
Posted on August 16, 2018 at 5:25 PM

Blackat USA vs DEF CON, Pros and Cons
It’s been a week since Blackhat USA 2018 ended. I was present that week and I found some really cool workshops that I haven’t had the opportunity to talk about. Some workshops where very dense, while others where very broad. A lot of companies where there to sell me their product, with mottos like “securing your endpoint” being said over a million times and then the annoying NFC badge scanning so they can send me mail spam with “want us to fix your spam problem?” as the subject header. Quite casual.
Blackhat USA is culturally divided from DEF CON. I think that has to do with the fact that DEF CON only costs around $200 while Blackhat costs over $2,000. This really separates the professionals that have the money to burn on publicity stunts versus underground hackers that are trading knowledge. Nevertheless, both conferences is a must-go experience for all researchers/hackers/analysts/etc. So let’s briefly talk about what I saw there.

Some of the Cringy stuff I saw
This is a picture I took of Rapid7’s booth where there was this hooded hacker with a really deep voice talking about identity theft or something. Not sure if it was an intended joke, but I was laughing.
Another thing that was kind of cringy was how a lot of companies where pushing the whole “dark web monitoring” phrase around. I noticed AlienVault was doing it, Norton’s Lifelock does it, a lot of companies do it. This has to be some marketing gimmick for those not so savvy users that throw money at all there problems. If you happen to see this at any conference, do what I do and ask them what it means exactly.
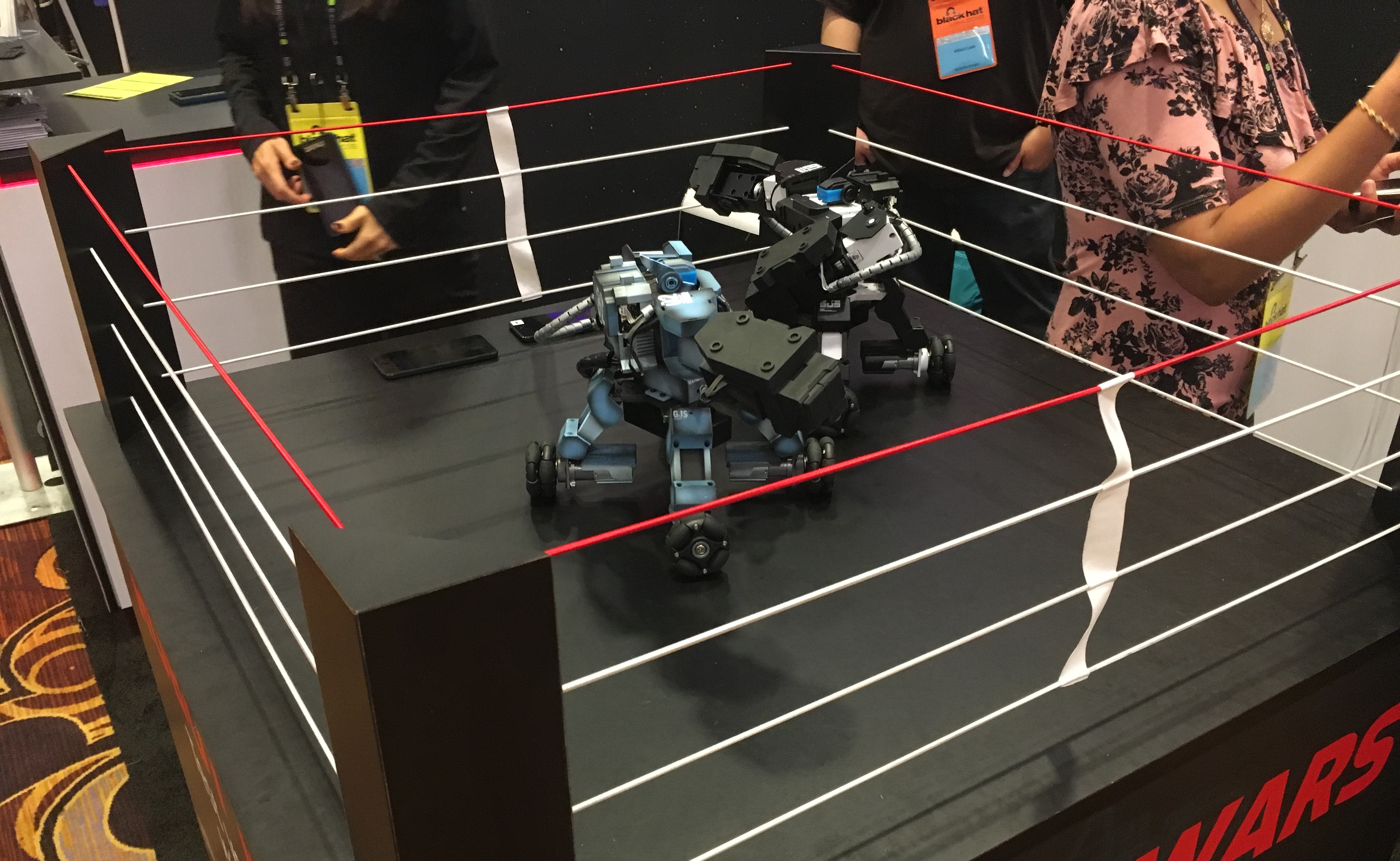
The Cool Stuff I saw
I forgot what booth this was, but there were two robots fighting to their deaths (which is ultimately what happened) and I thought that was really cool. I’ve always noticed that anything to do with robots really gets the crowd’s attention at these conferences. Just don’t overdo it with “powered by blockchain super AI” and you’ll gather a pretty decent crowd.
I don’t have a picture for this (you’ll just have to take my word) but I ran into the guy from Breaking Bad, Jonathan Banks. I know last year they had Christian Slater in Blackhat which was really cool.
If you hate company influenced booths, the best place to hang around in Blackhat is the Arsenal. The Arsenal is a dedicated place in Blackhat where researchers and hackers alike come to show off their findings in tools that they usually release for free. There where a lot of tools present for network analysis and assessment.
This was a video taken of ChipWhisperer, if you’re into embedded hardware security and side channel analysis, then I highly recommend you check out this project here. Side channel attacks have to do with the way in which a computer system is implemented on a hardware level. So think about the electromagnetic waves, the power consumption levels, and think about data leaking through those components. Usually this type of analysis is very “dense” or complicated in terms of understanding. I’m personally not that adept in side channel attacks.

This photo was taken from this year’s Pwnie Awards. I know very little about what the Pwnie Awards are, this one in particular was my first one. I did not know it was hosted annually in Blackhat. If you really enjoy hacker culture, I really recommend going to their annual ceremonies. The Pwnie Awards to sum things up is like the Oscars or Grammys but for security discovery and failures. That’s what makes the Pwnie Awards so good, is that the judges will award people in both realms. The funniest one was when John Mcafee won for “Lamest Vendor Response” for his Bitfi cryptocurrency hardware wallet that got hacked a million times (to which he still claims is unhackable).
The Blackhat Briefings
I attended numerous briefings and of course the keynote. A lot of them were very information heavy, in very specific branches of security. Unless you’re a super genius that knows everything from the depths assembly language hell to debugging the BIOS (not exaggerating), you’ll be lost at some points throughout the entirety of Blackhat. That’s not necessarily a bad thing, it just means you have a lot left to learn, which is why we love the InfoSec community.
One talk that I found the most informative (only because I understood everything) was the talk about web cache poisoning by James Kettle. Personally, I was going to implement a cache system for my web server to hold on data retrieved from API calls (to reduce API costs). I had no clue that it was possible to poison my cache in the way James had shown everybody at Blackhat. The live demonstrations alone where brilliant and I didn’t feel rushed or overwhelmed with information. James, if you’re reading this, great job!

Another talk that I really enjoyed was the one done by Ben Gras on TLBleed. Like I said earlier I don’t know much about side channel attacks, nevertheless they’re very crucial to conceptually understand in computer security. If you’re familiar with Meltdown, Spectre, Foreshadow, and are interested in CPU/microprocessor related vulnerabilities, TLBleed is definitely worth looking at.
Normally we overlook our threat model when it comes to things like hyperthread vulnerabilities, timing attacks, fault attacks (like Rowhammer). This vulnerability in particular can very much be used to leak encryption keys and other types of data. The most interesting thing about TLBleed is how it uses machine learning to analyze the TLB (a place that stores recently accessed memory addresses) to then steal data stored in those memory addresses. If you’re reading this Ben, fantastic job!
Overall, Blackhat USA was fun this year. I hope I get the opportunity to meet more people as the next conference resurfaces. Shoutout to all the people I ran into last week ;-)
InfoSec Related