LeakedSource Fiasco
by AKM
Posted on January 27, 2017 at 4:00 PM

LeakedSource shutdown by FBI
LeakedSource, a popular pay-to-access archive designed for searching through millions of databases for information has been shutdown. The reason? A police raid influenced by an FBI subpoena. FBI agents have retrieved all of LeakedSource's solid state drives containing all of their database archives. No word yet on why they have been shut down.
The site has been very popular amongst the "OG community" (OG = Original). A community destined for obtaining illegal access to accounts with "good looking usernames". Usernames that are common words or short on popular social media platforms like twitter have been accessed and sold on marketplaces like ogflip.com.
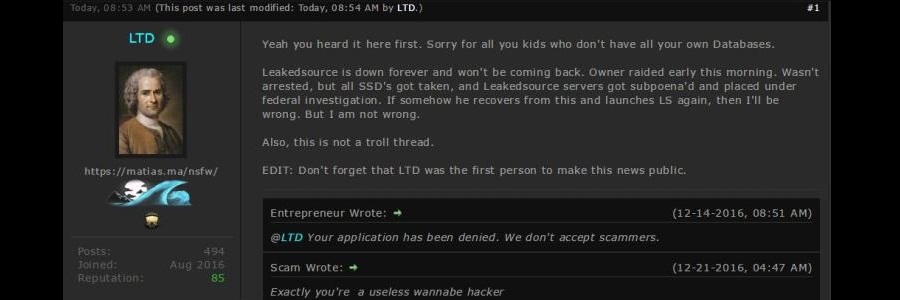
A post made by a user called “LTD” on ogflip claims that “Leakedsource is down forever and won't be coming back. Owner raided early this morning. Wasn't arrested, but all SSD's got taken, and Leakedsource servers got subpoena'd and placed under federal investigation”. Further analysis of LeakedSource’s presence shows it's been offline and the whois data still remains unchanged. CloudFlare seems to still be responding to requests (104.20.40.226) but the site itself is gone.
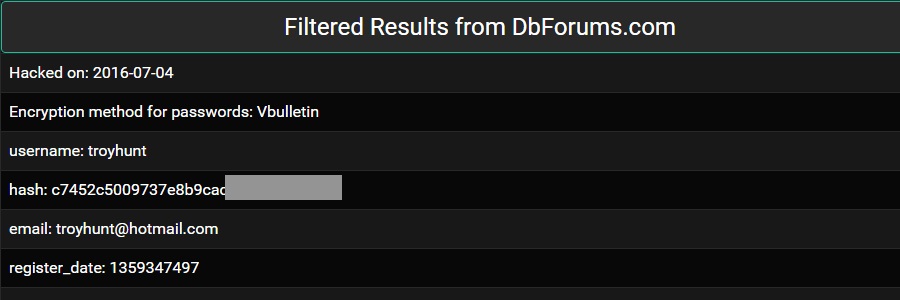
LeakedSource was a very important online tool for this community to thrive. When accounts needed access to, these so called “hackers” would often use LeakedSource to hunt down old passwords and then try reusing them to gain access (hoping that the primary owner of such account uses the same password everywhere). With just around 2 dollars would grant you access to the entire site's database archive. Some hashes are cracked, some are not. Just type in the email and you can search all you want until your subscription ends. Get the password, type it in on the account associated with the email, and there. You are done. Once access was gained on these “og accounts” the intruder would often take the necessary steps to secure the account (change email, passwords and maybe add 2 factor authentication). After that, they would either trade, sell, or keep it to themselves. Without it (if the community is to survive) , they would have to resort to keeping local copies of the would be databases.
More than likely the FBI will look through LeakedSource’s own database (usernames, emails, IP address, and passwords from LeakedSource itself) and hunt down alleged members of the site. We’ve seen this done before with Operation Shrouded Horizon and the Lizard Stresser takedown (were FBI agents hunt down easy to target subscribers of these services). The admins of LeakedSource are said to be under investigtaion but not yet under arrest.
What is expected to happen is sites that sell databases are more than likely going to get resurrected with the fall of LeakedSource and the remains of such popular demand for access to the archive. There is no clear cut site that offers the same service, smaller sites are expected to be formed with similar services as outcome.
A similar site that shows if emails, etc. that have been compromised is HaveIBeenPwned.com. A site made by Troy Hunt, a Microsoft employee and InfoSec blogger. His professional site, unlike LeakedSource, does not sell credentials or entries, it aims at warning users from breaches or compromise, “pwnage”. Troy also claims his site does not contain sensitive info, just the email lists. Its free, fast and actually useful. More information about HIBP can be found here.
InfoSec Related