Ploutus-D Malware Empties ATMs
by AKM
Posted on January 30, 2018 at 4:30 PM

Poutus.D Strikes Diebold ATMs
Ploutus is an unusual piece of malware that's designed specifically for ATMs. It first appeared in late 2013, criminals simply inserted a CD or HDD into the ATM’s own drive bay, restarted the system, and directly booted from the malicious drive. Quite basic. Sometimes it can also be done via USB tethering and instructions are sent via SMS (based off a variant in 2014). Ploutus even then had its own interface and everything, interactions to the ATM would be done off an external keyboard. Its primary objective is clear, to entirely empty an ATM machine.
 https://www.fireeye.com/content/dam/fireeye-www/blog/images/Ploutus%20Variant%20Daniel%20Regalado/Fig3.png
https://www.fireeye.com/content/dam/fireeye-www/blog/images/Ploutus%20Variant%20Daniel%20Regalado/Fig3.png
Quite odd seeing malware interacting with devices like so? No. ATMs have always been targeted for “jackpot” style attacks. Usually they are targeted through skimmers and other types of card intercepting hardware. The United States Secret Service just four days ago released a press statement on the ATM “jackpotting” attack threat. The press release states that “perpetrators must gain physical access to the cash machine and install malware, or specialized electronics” like external keyboards, USB tethering devices for SMS communication, and other human interface devices. Just recently a new variant of Ploutus was spotted on Virus Total. Dubbed by FireEye as “Ploutus.D”. The “D” because it specifically targets Diebold Nixdorf manufactured ATMs.
 https://www.secretservice.gov/data/press/releases/2018/18-JAN/GPA_01-18_ATM_Jackpotting_Attack.pdf
https://www.secretservice.gov/data/press/releases/2018/18-JAN/GPA_01-18_ATM_Jackpotting_Attack.pdf
Its interaction is almost identical to the previous variants. Controls are defined from the external keyboard’s function keys. The one everyone seems to be interested in is the one that causes the ATM to spew out all the cash, F3. Other function keys are for navigation and receiving the ATM’s unique identifiers. If you’re wondering, most ATMs do have safes that protect all the money, that’s why it’s quite difficult to break into one. The concept being expressed here is the fact that ATM electronic components are not protected so heavily. The hardware of the ATM does not reside inside a safe, it is relatively open for attack once the front panel is removed.
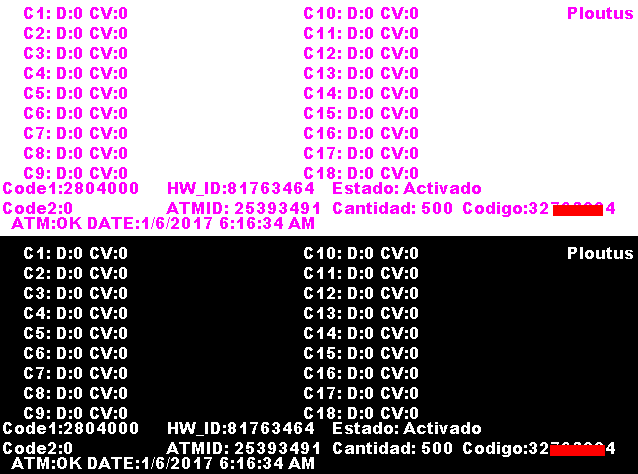 https://www.fireeye.com/content/dam/fireeye-www/blog/images/Ploutus%20Variant%20Daniel%20Regalado/Fig11.PNG
https://www.fireeye.com/content/dam/fireeye-www/blog/images/Ploutus%20Variant%20Daniel%20Regalado/Fig11.PNG
Although this style of attack is very complex, it’s also very high risk. Gaining physical access like previously mentioned requires either the correct set of generic keys used to open most ATM machines (hard to obtain) or specific keys (very hard to obtain) or brute force (requires strength). This is only to take the front panel off, once you’ve done that it’s a game of trial and error. This heist would take at least 10 minutes, if not 30. If any potential ATM robbers are reading this, plan your approach.
InfoSec Related