Petya or NotPetya?
by AKM
Posted on June 27, 2017 at 4:46 PM
NotPetya released into the wild
Nothing special here, just a bunch of unpatched Windows machines on "protected" internal networks. On second thought, why is there still a significant number of unpatched machines?! Have we not learned from WannaCry? Petya uses similar infection techniques found within the WannaCry Ransomware (more info here) but with a twist. Petya modifies the MBR (Master Boot Record) making the running Operating System inaccessable.
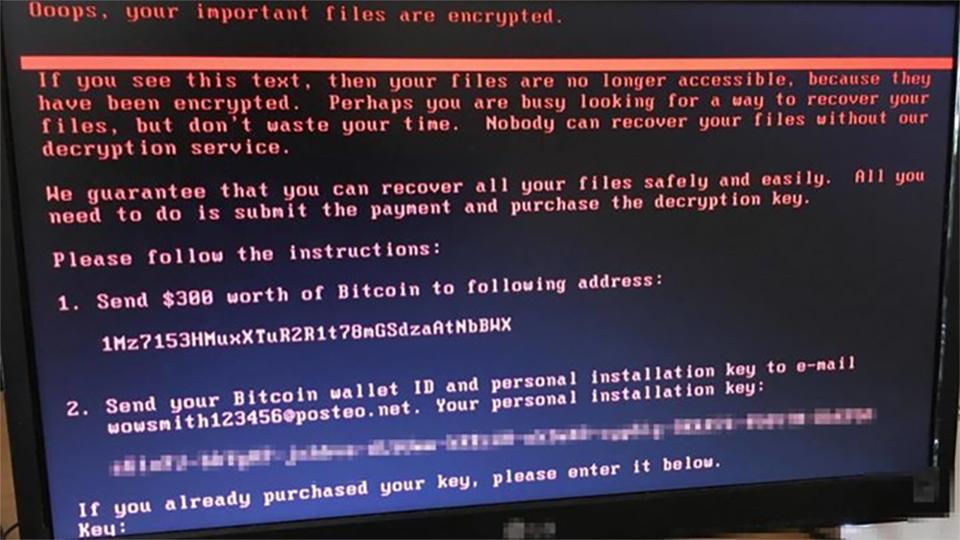
Wait so why is this one called NotPetya? Let’s take a trip back to 2016; Petya was originally a *working* piece of ransomware that just like this one, encrypts the system’s filesystem and then replaces the hosts MBR. The Master Boot Record is very important but also replaceable (in most occasions). It is what executes before the Operating System and holds vital information such as the sectors linked to an OS or the connection between alternative bootloaders like Grub. NotPetya is a little different. First of all, it’s not even appropriate to call it ransomware, it’s a wiper. It’s payload encrypts the filesystem and MBR without a valid way of retrieving files back. So ideally, total annihilation. This variant also uses the EternalBlue exploit just like WannaCry, the same exploit released by the Shadow Brokers (more info here). So what does this mean? It means it spreads just like WannaCry, through SMB onto unpatched windows machines (most of which running outdated Windows XP and Windows 7).
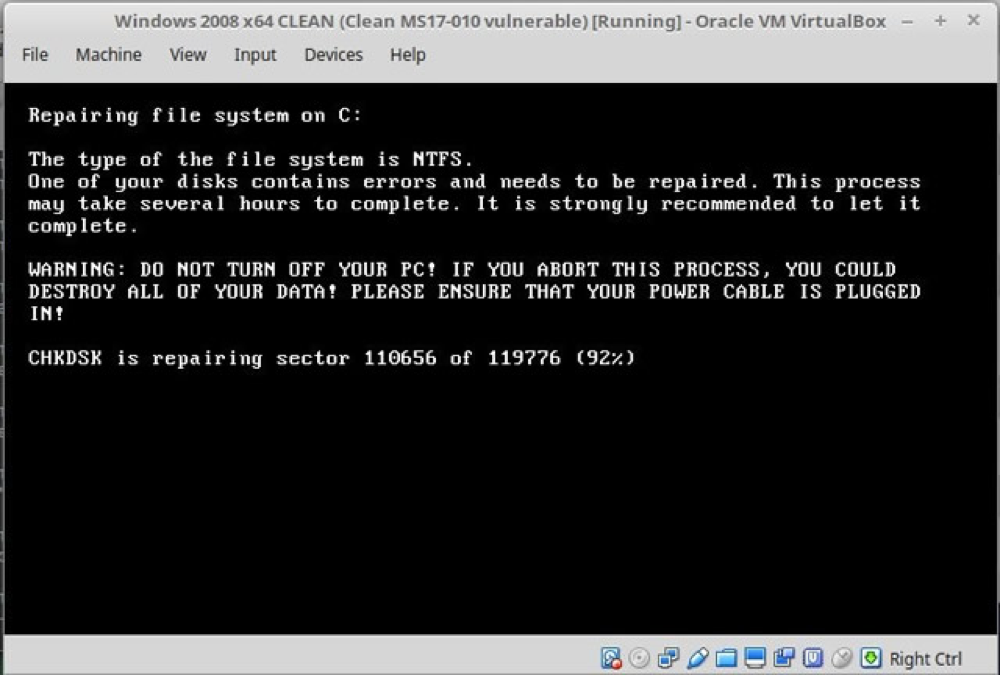
Once infected by NotPetya, files that aren’t in-use will become encrypted and then your device will be scheduled for a restart. Before your computer can restart, it will also infect all unpatched machines on the same network using EternalBlue exploit via SMB (just like WannaCry). Once restarted, NotPetya will display a screen pretending to be a CHKDSK (a disk check utility that finds bad sectors). CHKDSK scans the hard drive for faulty sectors, here NotPetya is using its name to encrypt your master file table which essentially makes recovery impossible.
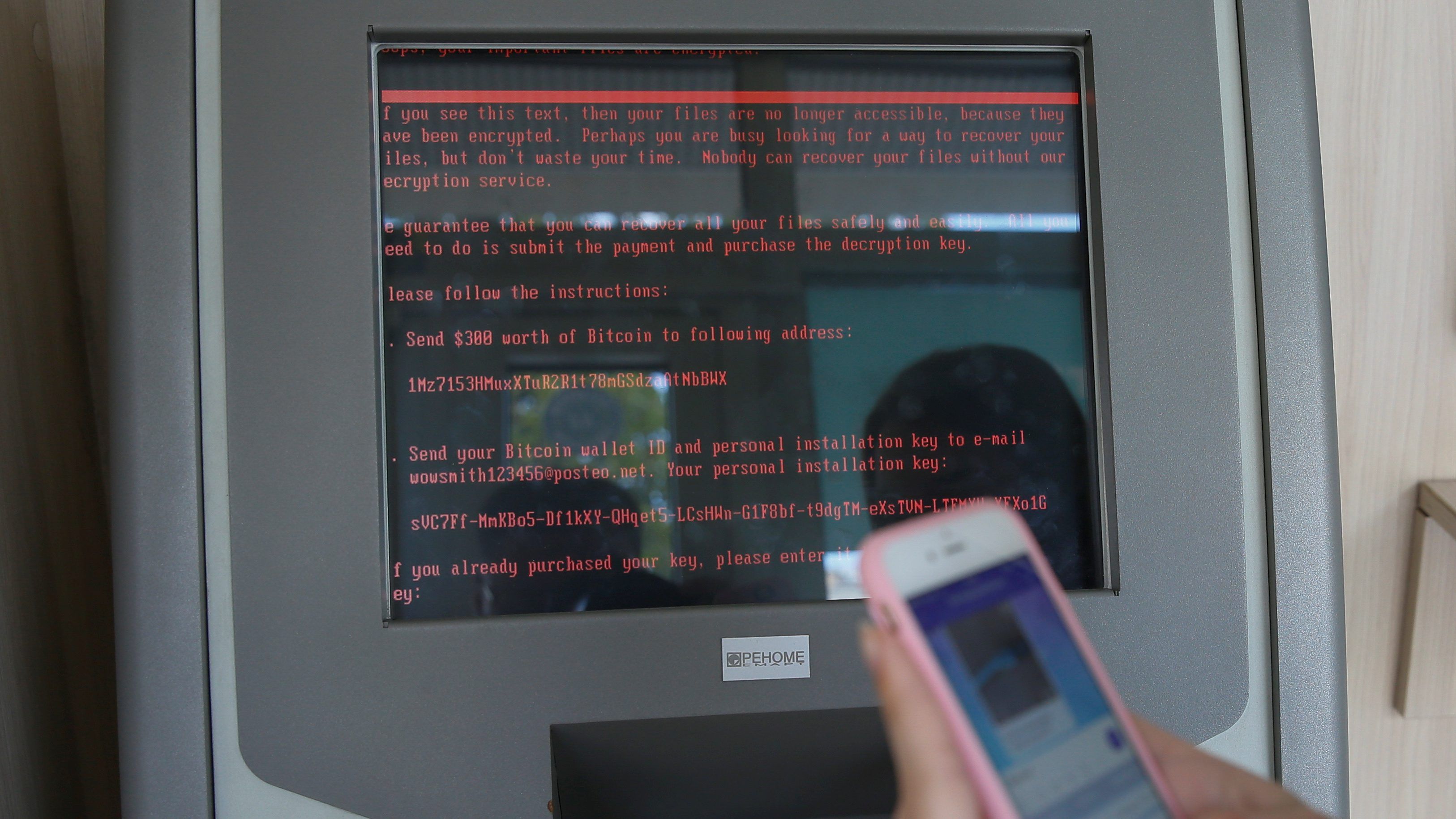
This variant of Petya also asks its victims to send $300 in bitcoin and an email to “wowsmith123456@posteo.net”. Here is the problem, yes you can pay the ransom but you will not be able to send an email to that address. Posteo earlier announced that access to that email has been blocked (here is what they had to say). Which means whoever made NotPetya, no longer has the ability to send out decryption keys. Regardless, the encryption technique used by NotPetya is designed to be irreversible. It’s entire purpose was to be released into the wild and be thought of as ransomware when in reality, it was a wiper all along.
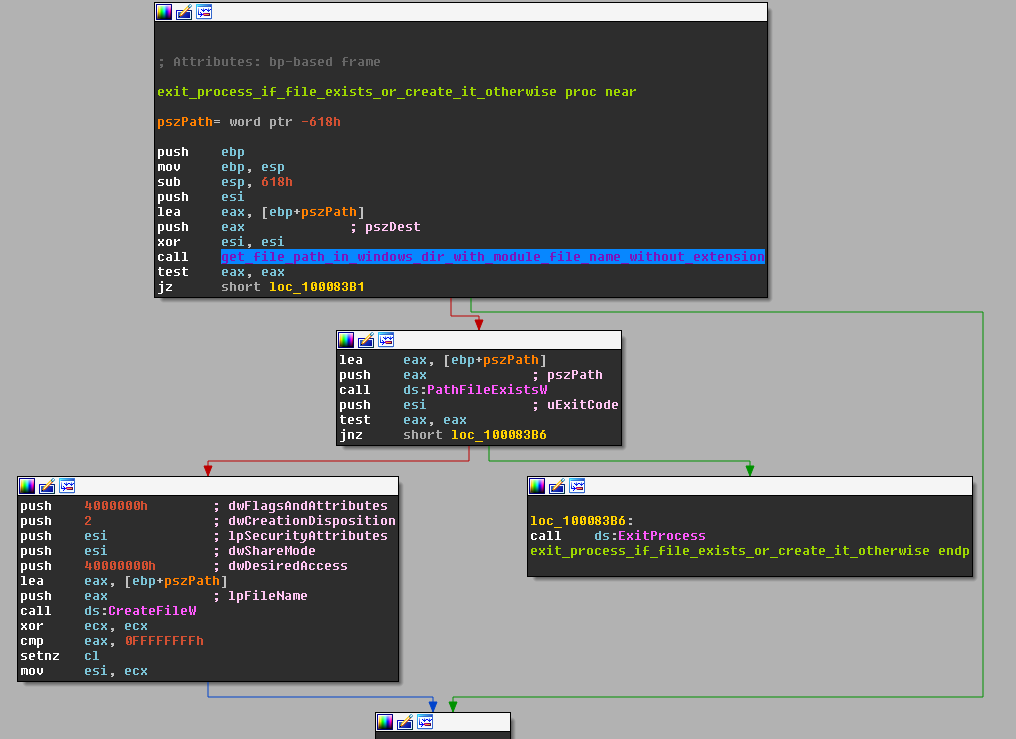
There has been found a kill-switch or vaccine for NotPetya by Amit Serper. All you have todo is create a file labeled “perfc” inside the C:\Windows\ directory. This file cannot have any extensions. Once created, it will block NotPetya from executing. This seems to work, however it should not be considered a replacement for Windows updates. Updating your machine is the most important thing to do when it comes to avoiding ransomware. Most of these widespread attacks all seem to be utilizing EternalBlue (the NSA SMB exploit) so don’t be surprised if you don’t update and eventually get infected by some other wiper/ransomware. Update your machines and protect yourself with Anti-Virus like Kaspersky. You shouldn’t have an excuse.
InfoSec Related