WikiLeaks "Hacked" by OurMine
by AKM
Posted on August 31, 2017 at 11:30 AM
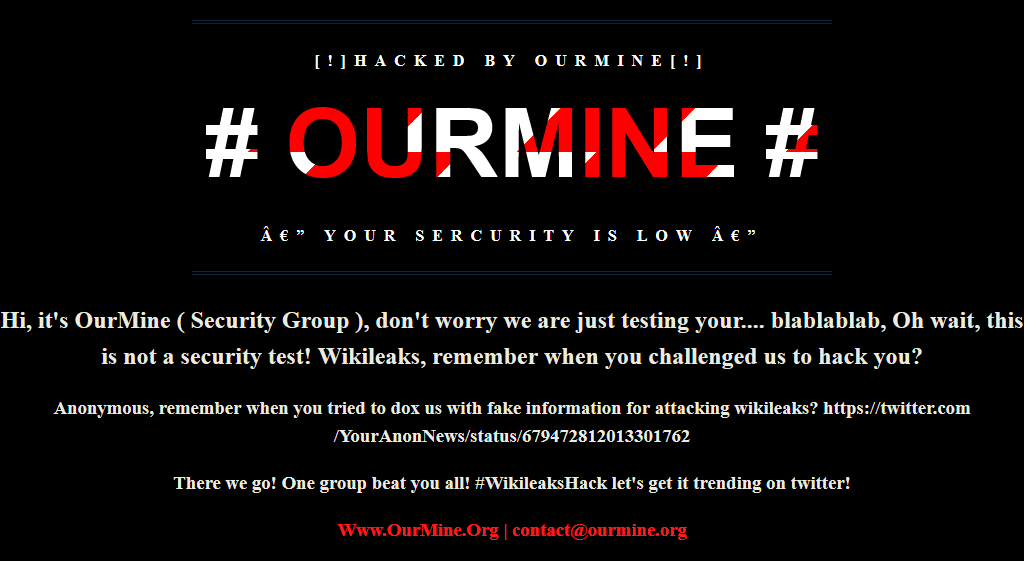
WikiLeaks DNS attack
This is the page visitors were presented with upon visiting WikiLeaks.org yesterday afternoon. Network routing analysis shows that traffic to wikileaks.org was being sent to 181.215.237.148 instead of the official servers located at 95.211.113.131. Clearly this was a DNS hijack, nothing more. At first glance, I recognized the group responsible. OurMine. No, they aren't threat actors, I personally wouldn't even call them professionals either. What makes this attack a little more significant than usual is the fact that it's WikiLeaks. Let's start off and clear some things up first, no WikiLeaks' internal servers were not breached and no, no one accessed their network what so ever. This is a very simple attack vector which results in changing DNS records.

Let's talk about OurMine for a bit. "They" started around 2014 but really began gaining attention around 2015. It was originally ran by one person that went under the alias "abody" aka Abdulrahman Makki. This isn't false information or anything like OurMine themselves claim, this was confirmed when their site ourmine.ninja had the email abody@ourmine.ninja attached (and used on multiple social media platforms like Skype). As time went on, OurMine's very own Abody got owned and the group came out to claim he was no longer apart of OurMine. This is were things get interesting, OurMine was and has always been known for using broken English (the lack of spelling and speaking) and low profile attacks (essentially hacking random celebrity accounts using old passwords found in breaches). OurMine never was responsible for anything high profile. It's very possible that this isn't the same OurMine.
You're probably asking why anyone would want to use OurMine's public image for notoriety, perhaps it’s to keep a low profile and direct attention elsewhere. Think about it, do you really think someone would go around wasting time typing "We are just testing your security!" on Jack Dorsey's twitter account? The potential that could have come out of these attacks is endless. I'm not influencing malicious intent what so ever but instead of defacing WikiLeaks, they could have easily re-made all the *@wikileaks.org emails to receive classified intelligence. When you can add or change DNS records, you can easily setup a CatchAll() system for email forwarding. You don't need access to the internal servers what so ever. And all the other hacks? There could have been some serious money made off just advertising material off the accounts. This type of tactic they are producing with the whole "We are just testing your security!" is nothing but skid rubbish.
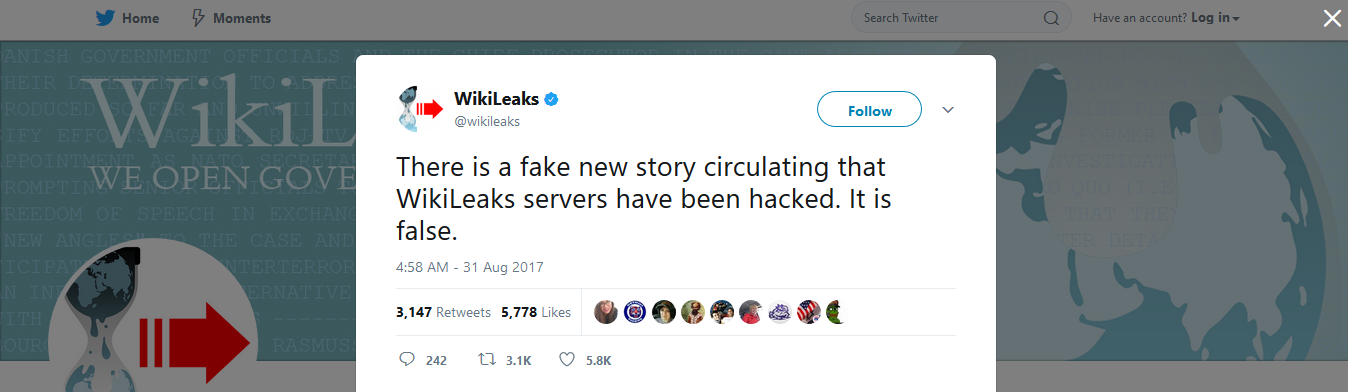
On a side note, both Assange and WikiLeaks have made public statements about how this indeed did not compromise any WikiLeaks' servers, rather it just shows that our current DNS is insecure. Remember to always check if the SSL certificate matches the one on the site, and also keep in mind one of the most secure forms of DNS is that of which the Tor Project implements in its hidden service .onion sites.
InfoSec Related