World's Biggest DDoS Marketplace Taken Down!
by AKM
Posted on April 25, 2018 at 11:30 AM

Operation PowerOFF
Webstresser.org was a site used by cyber criminals to wage large distributed denial of service attacks. All it took was a mere 18.99 USD or 15.00 EUR to start attacking any site of the user's choosing. For readers who are unaware of what DDoS attacks are, a DDoS attack is when multiple computers are commanded to start sending traffic to an unsuspected victim; once a certain amount of bandwidth is achieved, the victim's service looses connection to the internet because it doesn't have the capacity to withstand the attack. These attacks can affect anything connected to the internet, and can cause a lot of damage depending on what service is taken offline. Dubbed as "Operation PowerOFF", led by Dutch Police and UK's NCA (National Crime Agency), along with Europol and a dozen more international law enforcement agencies. Webstresser.org had servers located in the Netherlands, the United States and Germany, all of which have been seized and taken offline.

Webstresser.org was (according to Europol) one of the biggest marketplaces to engage in "DDoS-for-hire" schemes. Webstresser.org had well over 136,000 registered users! We can see the same aftermath witnessed when the notorious "Lizard Stresser" was taken offline, and the NCA went after registered users for a "friendly talk". In most jurisdictions, those who use such services can be prosecuted once tracked down. It isn't hard when Webstresser.org's user database contains fields for registration IP addresses and registration emails. Most who do register, do not take countermeasures into hiding their identities.
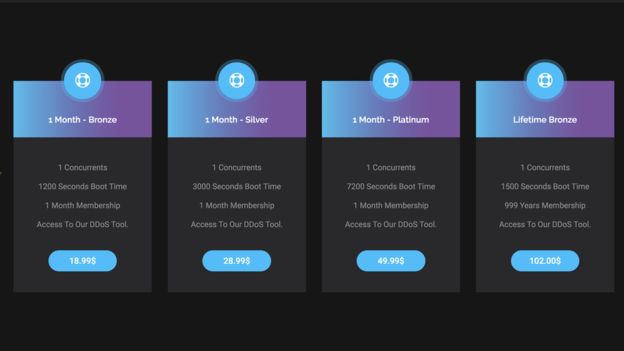
According to Europol, Webstresser.org had over 4 million attacks measured by April 2018. That's approximately 30 attacks per user. It's also important to note that between April 24 and 25, four admins of Webstresser were arrested. Although this is a big win for the law enforcement community, there still exists many other DDoS-for-hire services, a simple Google search will show just how many. Users of such services need to be aware that once the DDoS-for-hire that they are using is either compromised (hacked) or taken down by law enforcement, agencies will use that information obtained from the servers to track down users engaging in such attacks.
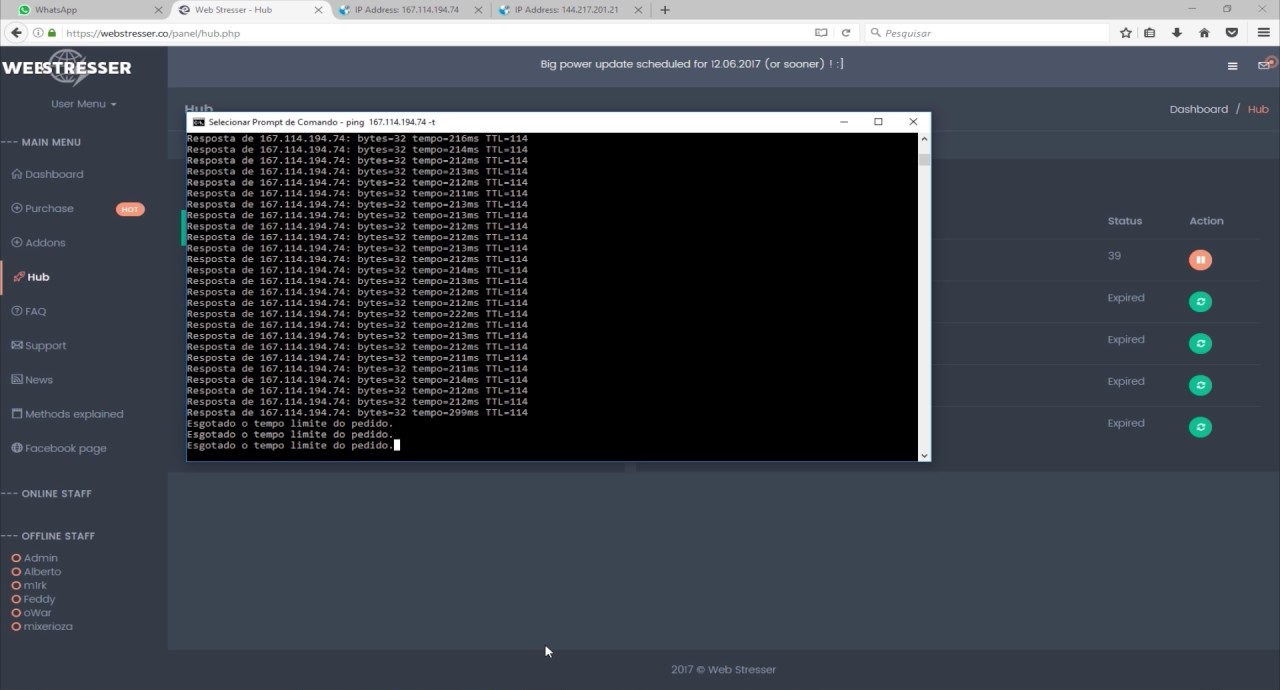
Here's a screenshot of a user engaging in such attacks using WebStresser. Whoever in this picture is being attacked can easily trace the attacker who initialized the attack. Usually most skids will "ping" the victim to see if they are offline, that ping in itself is enough for the victim to simply check traffic logs and take appropriate measures.
InfoSec Related