WannaCry Ransomware Attack
by AKM
Posted on May 14, 2017 at 3:15 PM
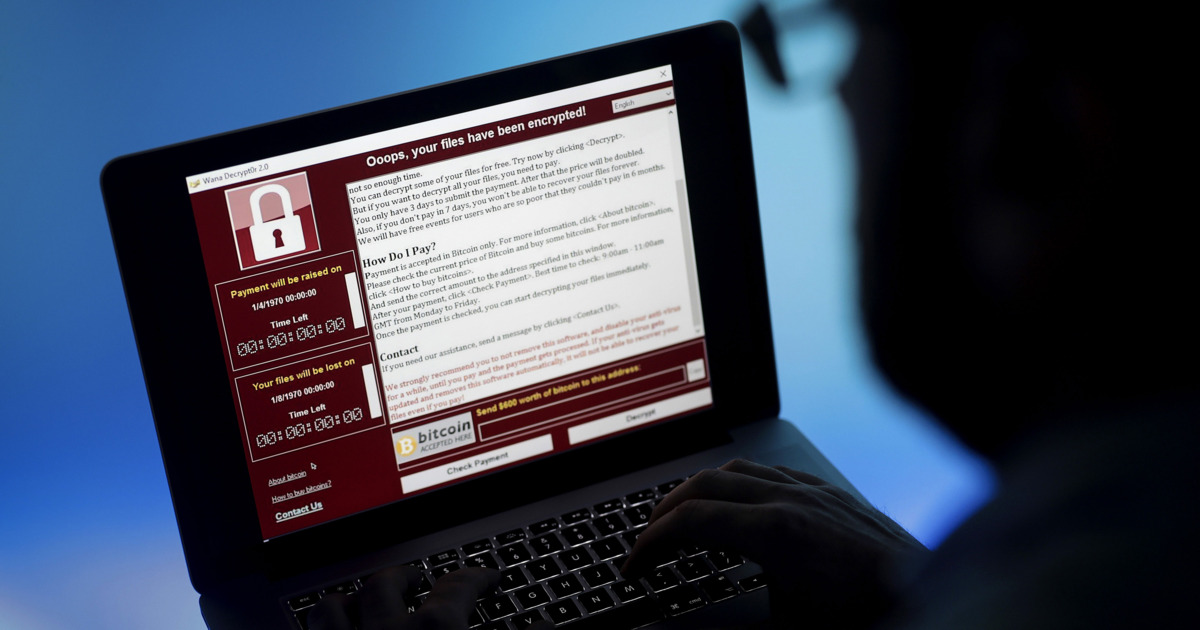
WannaCry Ransomware spreads like wildfire
Dubbed as "WannaCry" (initial name "Wana Decrypt0r") spreads to over thousands of Windows machines in 150 different countries. This type of malware is known as ransomware, a piece of malware that encrypts certain files (with specific file extensions) then asks for some currency in return of your files back. Essentially holding your computer hostage. There exists over hundreds upon thousands of diverse types of ransomware but WannaCry is very special.
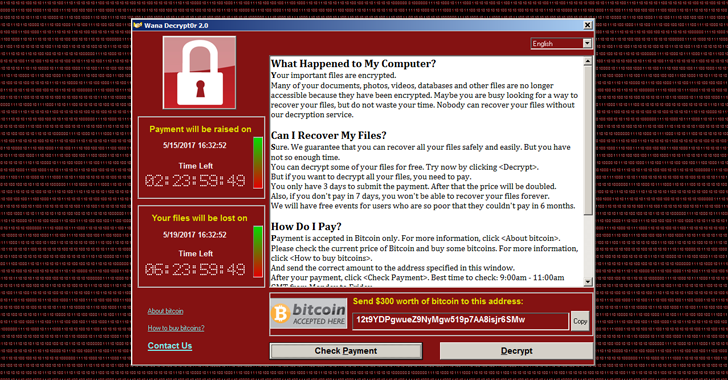
WannaCry uses a Windows exploit that was created by the NSA's Equation group called EternalBlue (more info can be found here). What this exploit allows WannaCry to do is spread via SMB, a file transfer protocol used since Windows 95. WannaCry is capable of spreading to outdated Windows machines that are connected to a network with port 445 open. Once WannaCry infects one computer via SMB, it begins to scan internal IP addresses on the same network and infects those computers as well. To sum things up, if port 445 is open, WannaCry enters the network and uses the EternalBlue exploit, infects one computer, then spreads to every other computer on the same network.

Once infected, WannaCry begins encrypting your files. Once it finishes this task, you are given the notorious display of what has happened and how you can fix it. The Windows popup urges the victim to pay via Bitcoin. If the victim doesn't pay within 7 days, the decryption key stored inside the operator's CnC server will be deleted. Keep in mind even when the victim does pay the amount specified, in order to begin the decryption process, a person on the other side has to physically send you the decryption key, which means it's never a full proof solution. Blogger and tech specialist "MalwareTech" managed to stop a significant amount of the ransomware from spreading by creating a sinkhole. Created almost accidentally due to WannaCry's own coding error, MalwareTech registered a domain that was hardcoded within the ransomware. What was more surprising is how the domain that was discovered by him did not change within the ransomware program, it was rather persistent. Later on, a new variant of WannaCry was released without this "kill-switch".
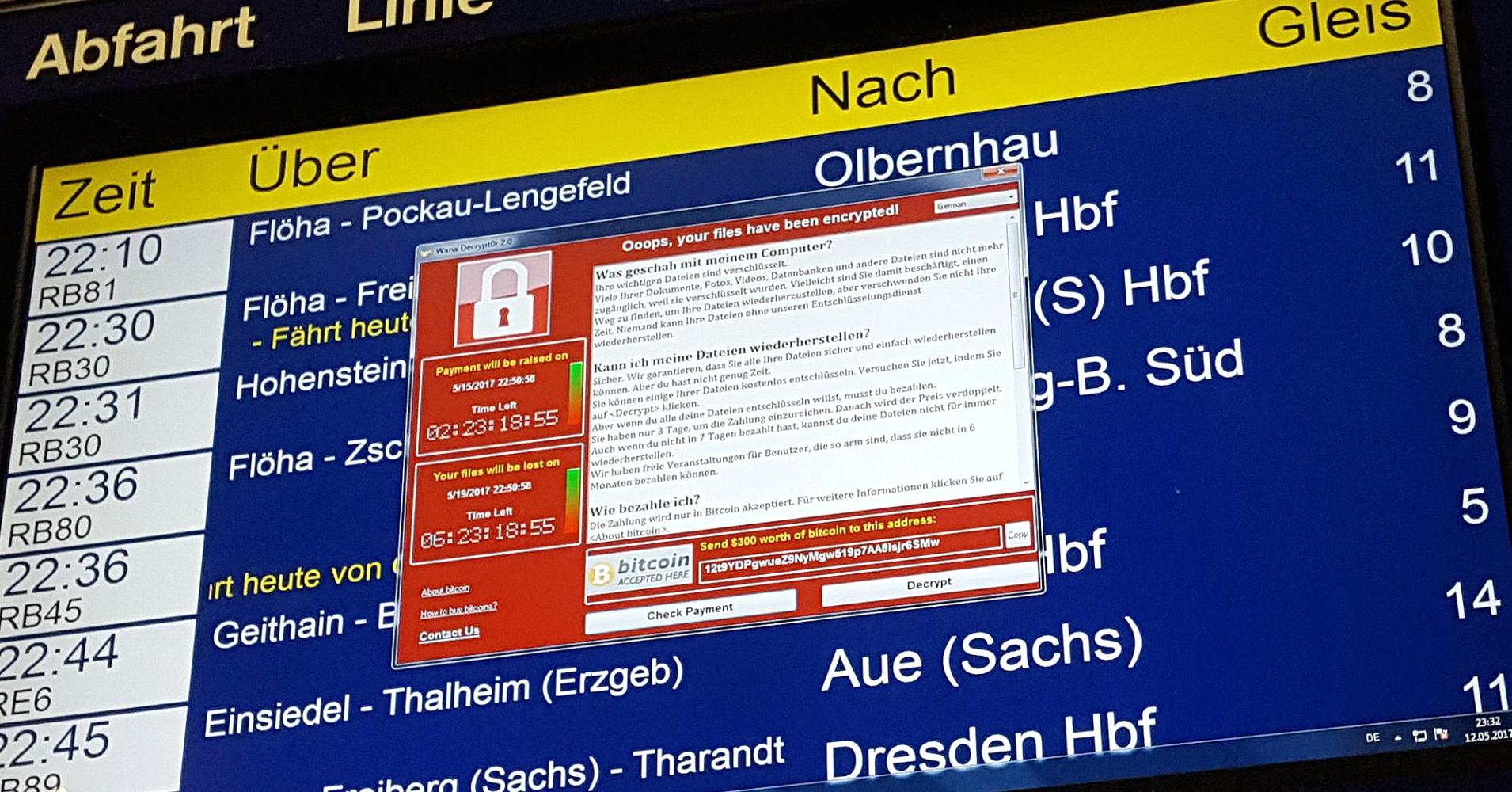
So what does all of this mean? It means if you're on a Windows machine that hasn't been updated since October 2016 then prepare to get owned by WannaCry. It also proves that Operating System updates are essential and not just an annoying concept that bugs you every five minutes. Security patches and updates need to be taken seriously especially on a corporate level. A hospital was affected by this ransomware in the early stages, what if it were a bank? Hinting towards some sort of Mr. Robot era here now are we?
Update: For all you lucky outdated machines that are still affected by this, there has been a new tool created for decrypting all your files! Go here for more info. Credit to HackersNews for the video.
InfoSec Related