XSS Vulnerabilities Found in Multiple .edu, .gov domains
by chandler
Posted on May 22, 2018 at 4:45 PM
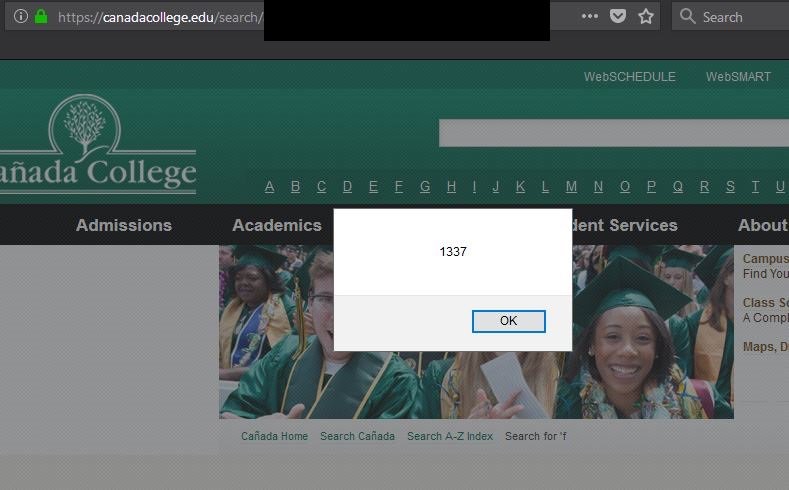
Various .edu and .gov sites pwned
We are constantly reminded that academia and government sectors have not yet reached the level of security you’d see in private companies. This is quite alarming since these systems protect not only private but also classified information. There’s a lot an attacker wants with the .edu and .gov domain space, here we explore endpoints we can leverage for a multi stage attack.
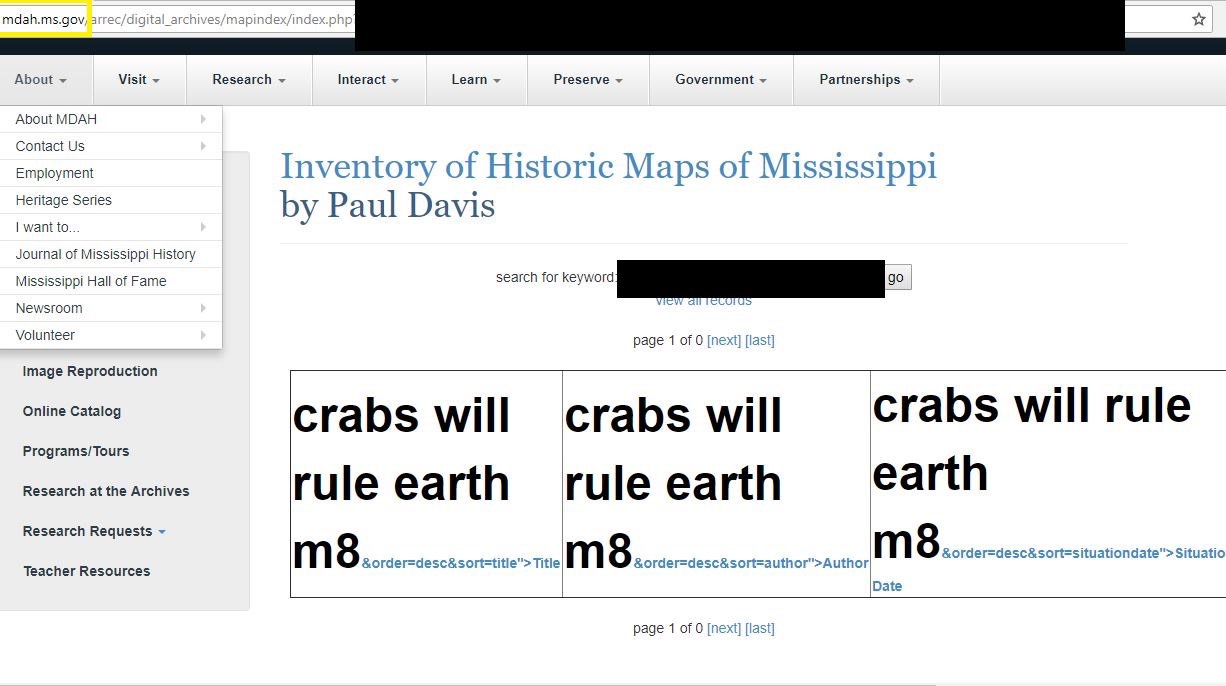
I recently discovered a Cross Site Scripting (XSS) vulnerability in the websites, http://skylinecollege.edu/, http://mdah.ms.gov/, http://canadacollege.edu/, and http://titan.apiit.edu.my. These vulnerabilities can be malicious if an attacker injects JavaScript code into the payload when a user clicks on the link it can execute the attacker's malicious code. There are many payloads an attacker can leverage, one popular type of execution resides within Monero miners (as we’ve seen the increase in government sites being hijacked for mining purposes). XSS vulnerabilities can also compromise account security by stealing cookies. Attackers could also redirect users to a malicious source of code or a different website.
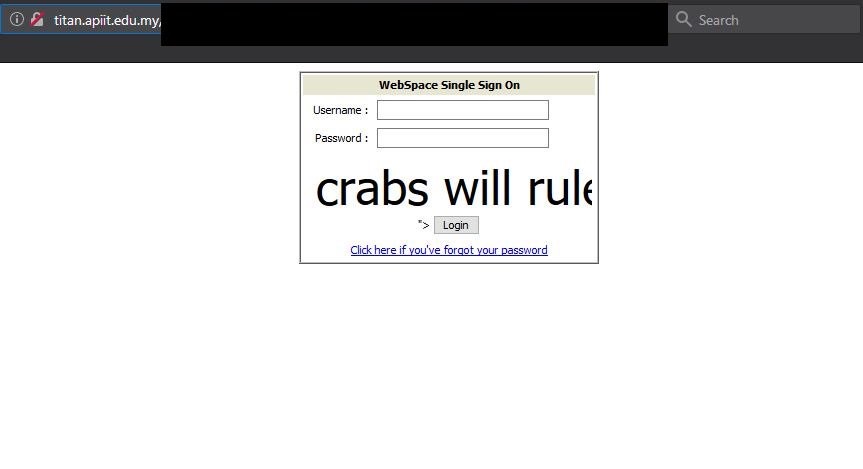
XSS can be very useful in phishing attacks as well, especially in the .gov and .edu realm. Gaining access to mail accounts through open redirect vulnerabilities paired with XSS is a gold mine for any savvy phisher. XSS also found on login panels (like on titan.apiit.edu) are good for siphoning credentials (since malicious JavaScript can be rendered). Overall, the owners of these sites should be aware of the coherent vulnerabilities present on their site and patch them as soon as possible.
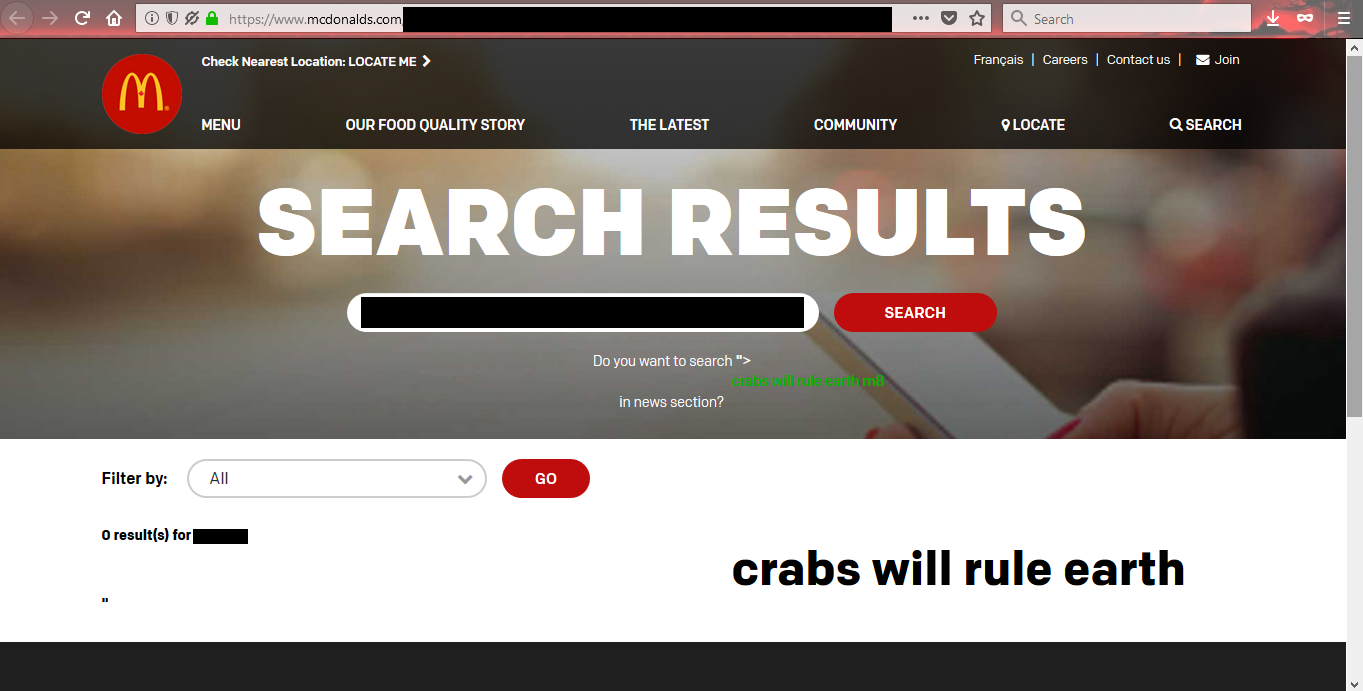
RIP McDonalds
Oh, and just for hugs and giggles, sorry McDonalds. Nobody is safe. Crabs will rule earth.
InfoSec Related